Mastering ethical hacking in software testing means gaining both strategic insight and technical proficiency to secure applications against malicious hackers. It entails utilizing a variety of technologies, putting good principles into practice, and incorporating security into each stage of the QA lifecycle.
Ethical hacking is being used by security experts and modern QA teams to go beyond functional testing. Network infrastructure security professionals are strengthened by testers simulating real-world assaults using methods including penetration testing, vulnerability assessment, reconnaissance, and exploitation.
What’s next? Keep reading to discover:
📌 Why Ethical Hacking Matters – The role of ethical hacking in enhancing software security and QA.
📌 Core Techniques Explained – Penetration testing, vulnerability assessment, reconnaissance, enumeration, and exploitation.
📌 Selecting the Right Tools – Choosing pen testing frameworks, exploit automation, and vulnerability scanners.
📌 Integrating Ethical Hacking into DevSecOps Workflows – Embedding penetration testing, continuous security checks, and automated QA into CI/CD pipelines.
📌 Enhancing Security Testing with Reporting and Debugging Automation – Using structured reporting and continuous feedback to identify and fix vulnerabilities.
📌 Advancing Your Ethical Hacking Skills Through Continuous Learning – Exploring certifications, real-world testing experience, and secure coding practices.
Frequent ethical software hacking activities guarantee better, more secure software releases in addition to improving quality assurance.
Introduction to Ethical Hacking
In the current digital age, software security is a top concern for businesses everywhere. Ethical hacking enables the discovery and correction of software defects before malicious actors may exploit them.

How Ethical Hacking Enhances Software QA Through Simulated Cyberattacks:
- Using hacking tools and methods to mimic actual cyberattacks is known as ethical hacking.
- Professionals carry it out with tools like free hacking software and ethical hacking software for defensive and legal reasons.
- QA professionals gain ethical hacking skills through training programs and practical labs.
- In software testing services, ethical hackers take the initiative to make sure apps are secure before being made public.
- Adding security-focused insights to the testing process, it enhances QA software testing.
Organizations can enhance their overall security and shield consumers from potential dangers by including ethical hacking into software testing techniques.
The Role of Ethical Hacking in Strengthening Software Security
Ethical hacking helps create robust programs from the ground up in addition to revealing security vulnerabilities. Enhancing program quality, integrity, and user trust is made possible by this useful tool.
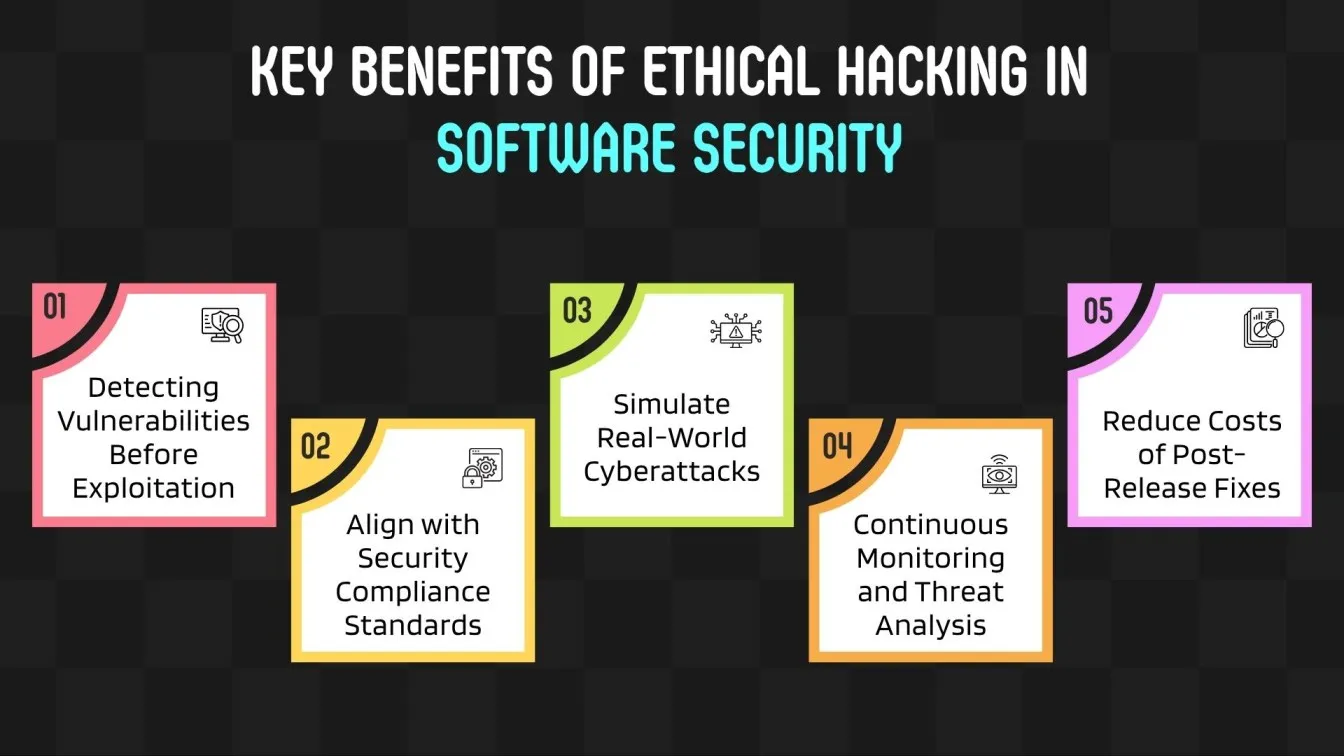
Proactively Identifying Vulnerabilities with Ethical Hacking in Software Development:
- Early on in the development process, ethical hacking identifies common vulnerabilities and exposes them.
- Combines security testing technologies with software testing methods to discover potential flaws.
- Targets OWASP Top 10 vulnerabilities to prevent cyber attacks like dictionary attacks.
- Enables ongoing security checks through automated QA testing integration.
- Models threats and tests defenses using penetration testing tools.
- Delivers detailed reports with clear, actionable insights.
- Aligns with industry standards for secure, quality software releases.
Every step of the QA and testing services pipeline is enhanced by successful ethical hacking.
Ethical Hacking vs. Malicious Hacking: Key Differences Explained
Security awareness depends on knowing the difference between malevolent and ethical hacking. Although they both employ comparable instruments, they differ in terms of authorization, legality, and intent.
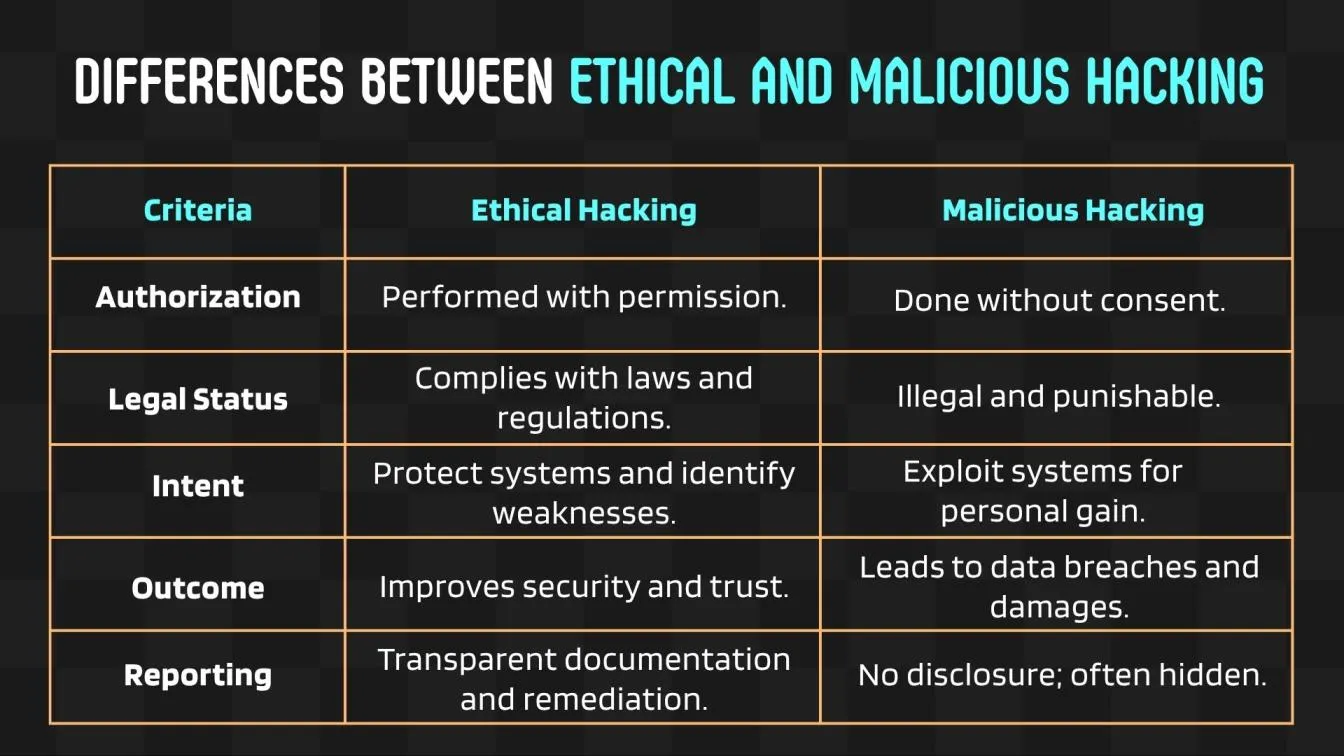
Ethical Hacking vs Malicious Hacking: Key Distinctions in Software QA
- While ethical hacking software is used with permission, malicious hacking is not allowed.
- Ethical hackers look for and fix flaws rather than taking advantage of them.
- Ethical hackers employ approved and documented pen-testing tools.
- While ethical hackers seek to defend themselves, malicious hackers employ hacking software to steal.
- Ethical hacking is used in software QA testing procedures to enhance product integrity.
Understanding these distinctions enables companies to appreciate ethical hacking as a valid security measure.
Identifying Common Software Vulnerabilities Through Ethical Hacking
Finding and fixing software flaws is mostly dependent on ethical hacking. If these defects are not fixed, they may be taken advantage of and lead to significant security breaches.
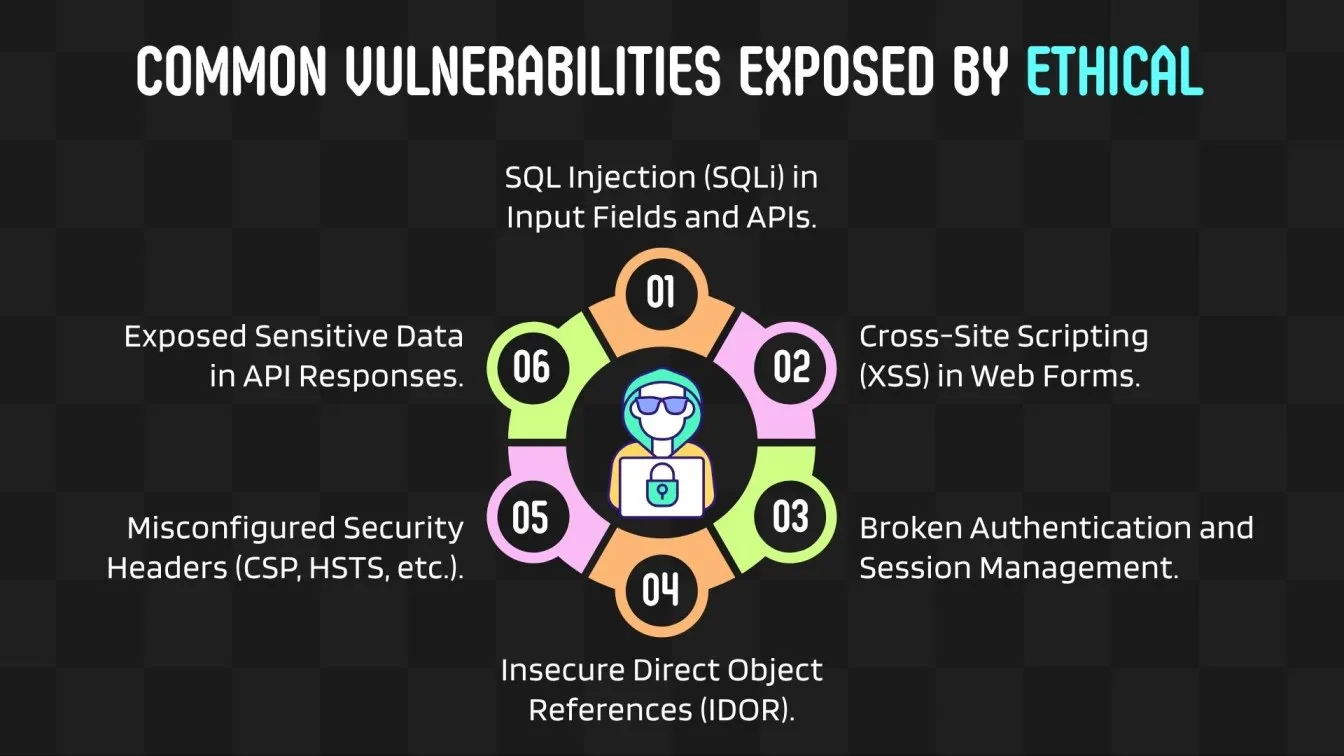
Identifying and Addressing Software Vulnerabilities with Ethical Hacking Tools:
- Tools from the Known Exploited Vulnerabilities Catalog are used by ethical hackers to find known vulnerabilities.
- Secure development is ensured by OWASP and source web application security checks.
- Penetration testing tools with advanced features uncover flaws in network infrastructure, apps, and API's.
- Ties into automated regression testing for real-time feedback and progress monitoring.
- Boosts QA accuracy with practical insights from found vulnerabilities.
- Includes Active Directory configurations among many more systems.
- Follows practice guidelines from trusted practice organizations.
Early vulnerability detection reduces risk and guarantees safe software delivery through ethical hacking.
Choosing the Most Effective Ethical Hacking Tools for Your Project
The effectiveness of your ethical hacking attempts might be significantly impacted by the tools you use. The size, scope, and security needs of the project all influence the choice of tool.

Top Ethical Hacking Tools for Effective Penetration Testing and QA Integration:
- Metasploit: Popular for exploit simulation and penetration testing.
- Nmap: Key tool for network scanning and vulnerability detection.
- Wireshark: Network traffic analyzer for security and debugging.
- Burp Suite: Widely used for web and API penetration testing.
- Network & API Penetration Tools: Support testing across multiple layers.
- Free Tool Versions: Ideal for training and small projects.
- QA & Automation Integration: Works with software testing and CI/CD pipelines.
- Vulnerability Scanning & Remediation: Focus on tools offering scanning plus fix management.
Early vulnerability detection reduces risk and guarantees safe software delivery through ethical hacking.
What Is Penetration Testing and Why It Matters in Ethical Hacking
A controlled attack simulation called penetration testing, or pentesting, is used to find weaknesses. It's a fundamental component of ethical hacking that guarantees software resistance to online attacks.

How Penetration Testing Identifies Security Flaws in Applications and Infrastructure:
- Pen testing finds software flaws from the viewpoint of an actual attacker.
- Pentesting tools mimic network, application, and API assaults.
- Comprises online application testing, network pentesting, and API pentesting.
- Aids QA teams in verifying system hardening while the software is being tested.
- Improves the identification of both new threat vectors and known vulnerabilities.
Better security posture and regulatory compliance are ensured when pentesting is integrated into software QA.
Responsibilities of an Ethical Hacker in the Software Testing Process
Modern QA teams benefit greatly from the insights and defenses against cyber threats that ethical hackers bring to the table. They collaborate with testers and developers to protect software at every level.
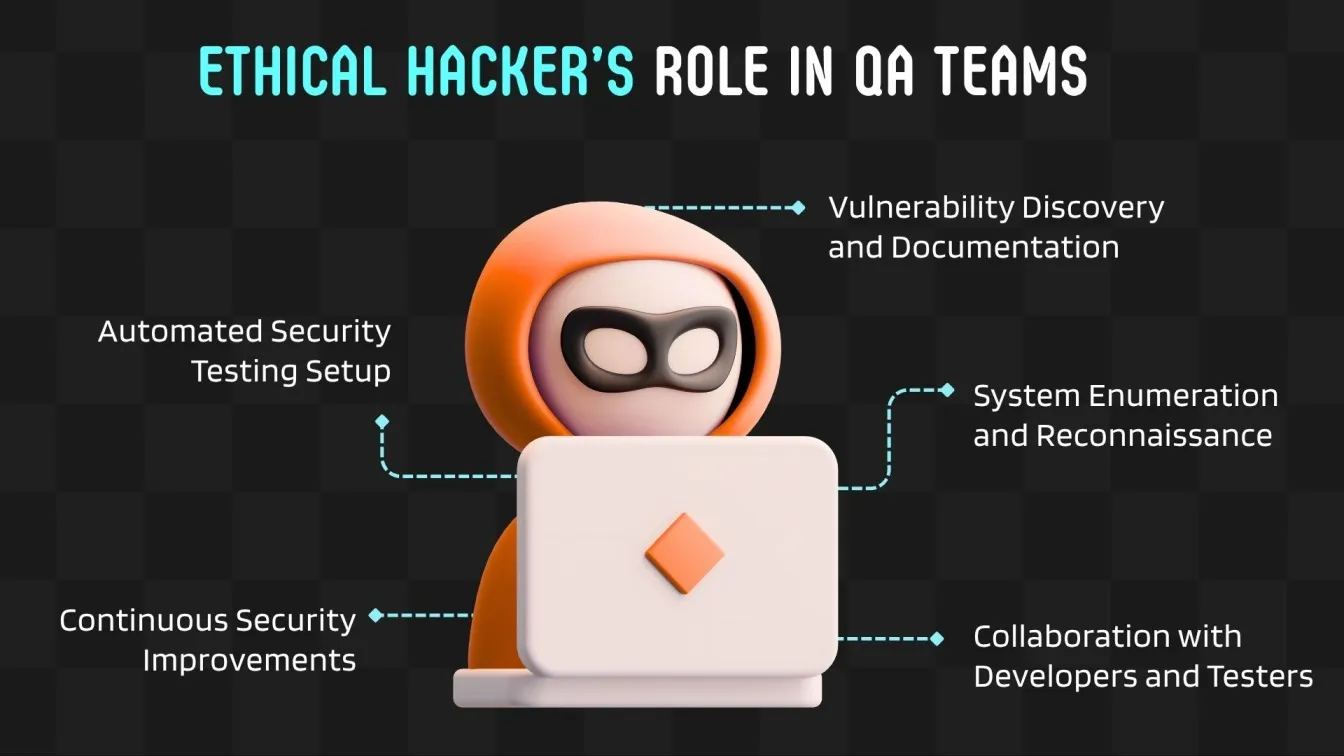
Ethical Hacking Process: Vulnerability Detection, Reconnaissance, Penetration Testing & QA Support
- Detect Vulnerabilities: Use application security scanners to find and log potential vulnerabilities.
- System Mapping: Perform initial network exploration and port scanning to identify weak points in wired and wireless networks.
- Simulate Attacks: Run tests with penetration testers to mimic real threats and assess defenses.
- Support QA: Share findings for patching and debugging within QA workflows.
- Enable Automation: Set up continuous monitoring tools to support secure CI/CD.
- Follow Effective Practices: Ensure alignment with modern security and QA business practices.
These duties guarantee that QA testing tools fix serious security vulnerabilities in addition to finding problems.
A Step-by-Step Guide to the Ethical Hacking Process in Testing
A systematic approach that is in line with software QA workflows is used in the ethical hacking process. This guarantees effectiveness, adherence to the law, and results that can be put into practice.
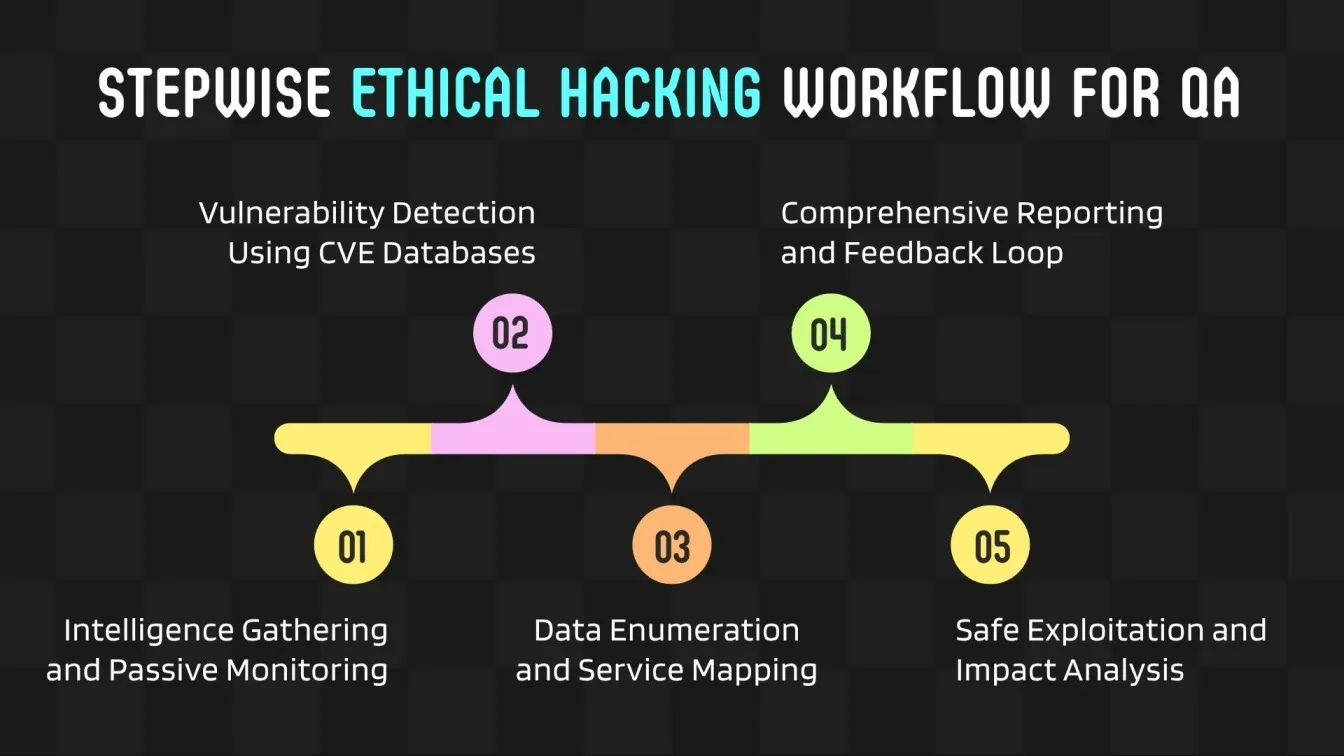
Key Stages of Ethical Hacking:
- Reconnaissance: acquiring intelligence both passively and actively.
- Enumeration: Data extraction, such as machine names, services, and usernames, is known as enumeration.
- Vulnerability Analysis: Use tools and CVE databases to find vulnerabilities.
- Exploitation: Using penetration testing software, safely exploit security flaws.
- Reporting: Records of developer comments and QA testing services.
By using this methodical approach, ethical hackers can make a valuable contribution to QA and testing services.
Legal and Safe Best Practices for Ethical Hacking in Software QA
Adhering to legal guidelines is essential when conducting ethical hacking. This protects both the organization and the ethical hacker while maintaining testing integrity.

Ethical Hacking Guidelines: Legal Compliance, Authorized Tools, Data Privacy & Industry Best Practices
- Always operate under signed agreements and a defined scope of work.
- Use only licensed or free hacking software with proper permissions.
- Avoid personal data access unless explicitly authorized in QA automation testing services.
- Observe NIST, OWASP, and other compliance standards' best practices.
- Integrate ethical hacking into existing software testing methodologies responsibly.
These best practices ensure ethical hacking is conducted safely, legally, and effectively within QA environments.
Conclusion: Utilizing Ethical Hacking for Robust Software Quality Assurance
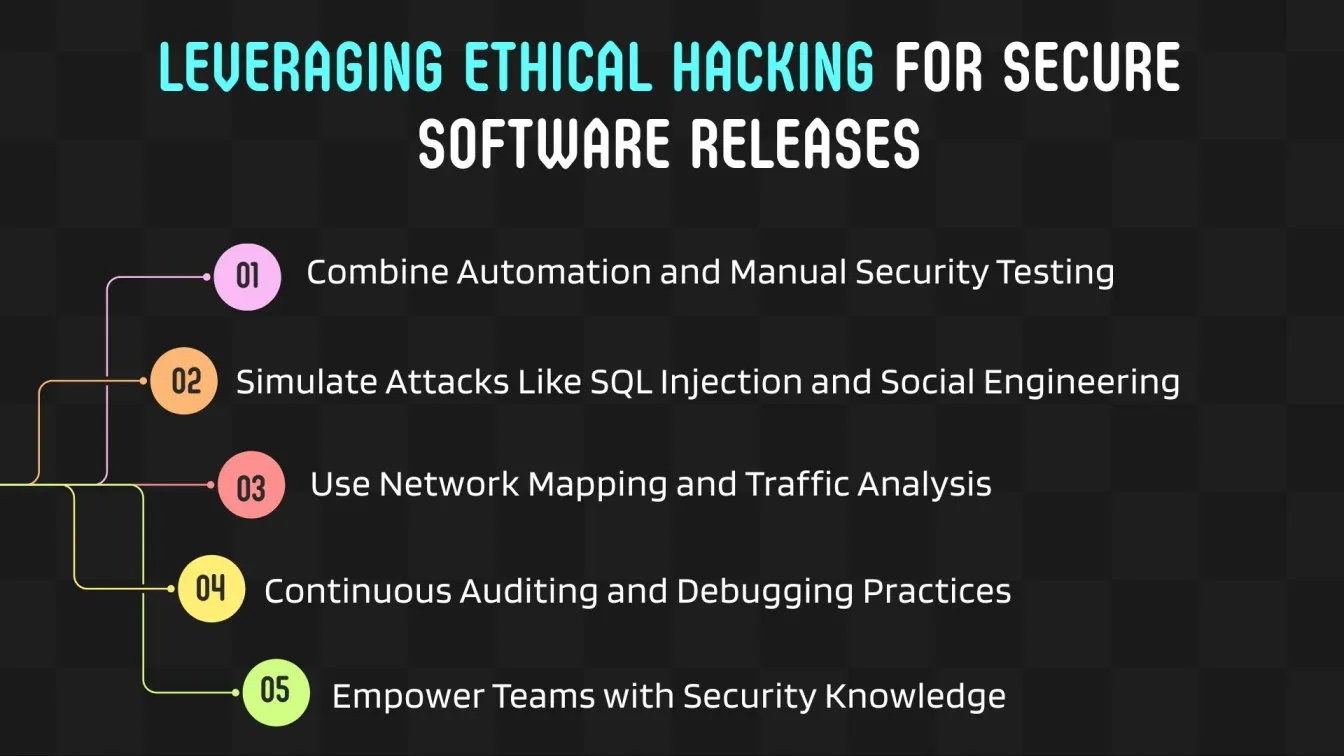
Ethical hacking enhances the software testing lifecycle by identifying prospective and existing security flaws. Using network scanning techniques, port scanners, and application security testing tools, it supports QA, software regression testing tools, and performance testing tools. White hat hackers strengthen defenses by simulating real-world cyberattacks like dictionary assaults, social engineering attacks, and SQL injection. Advanced command-line tools and network mapping aid in network traffic and infrastructure analysis.
To improve your cybersecurity posture, ethical hackers follow industry norms, conduct security audits, and deliver detailed reports. Combining workflow automation, USB debugging, and pen testing tools leads to faster releases and more secure applications. Gain hands-on experience with security-focused programming languages and tools to master ethical hacking in QA.
At Frugal Testing, we offer expert ethical hacking services tailored for software QA, helping you proactively uncover vulnerabilities before attackers do. Our penetration testing solutions and security-focused QA services ensure your applications are resilient, compliant, and release-ready.
People Also Ask
How do ethical hacking tools and techniques enhance the effectiveness of software testing?
Ethical hacking tools and techniques provide QA teams with actionable insights by simulating real attack scenarios, helping to uncover hidden vulnerabilities early in the software testing lifecycle.
What are the upcoming trends in ethical hacking for software quality assurance?
AI-driven vulnerability discovery, automated penetration testing, and incorporating ethical hacking into DevSecOps pipelines are examples of emerging concepts.
Which challenges do teams typically encounter when using ethical hacking in software testing?
Keeping legal compliance, integrating ethical hacking into current QA workflows, and a shortage of qualified personnel are common obstacles.
Which certifications and skills are needed to work as an ethical hacker in software testing?
CEH, OSCP, and CISSP are important credentials, and proficiency in penetration testing, vulnerability assessment, and secure coding techniques are also necessary.
What best practices should organizations follow to integrate ethical hacking into their software QA process?
Organizations should adopt continuous security testing, select appropriate penetration testing tools, ensure collaboration between security and QA teams, and automate vulnerability assessments within their software testing workflows.




%201.webp)

