Battling security threats alone?
Book a meeting now to detect, defend, and deliver excellence with our Security Testing
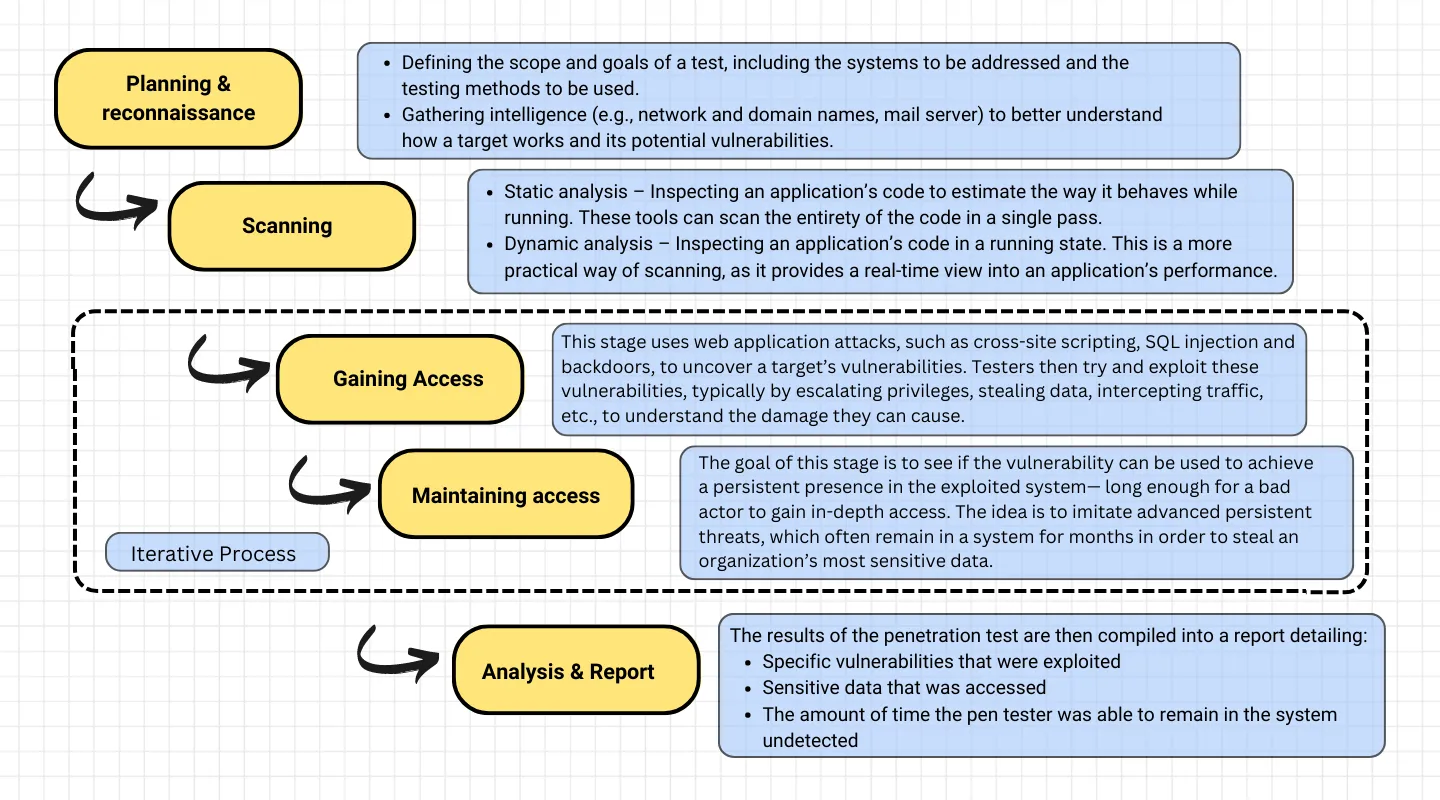
Security test failures can stem from various factors. Rapidly evolving threats, limited testing scope, misconfigured security controls, and lack of realistic scenarios can all contribute to vulnerabilities. Human errors in code or configuration, inadequate patch management, and insufficient security awareness also play a role. Complex system dependencies and lack of continuous monitoring further compound the issue. By implementing robust security measures, regular updates, and comprehensive testing strategies, organizations can mitigate these challenges and bolster their defense against evolving threats :

Risk Mitigation:

Regulatory Compliance:

Customer Trust:

Brand Reputation:

Cost Savings:
In today's digital era, where online transactions are flourishing, the stakes for maintaining robust cybersecurity have never been higher. A single security breach can result in the loss of customer trust, revenue, and even reputation. To stay ahead in the competitive landscape, organizations must prioritize the integrity of their data and protect it from unauthorized access. Frugal Testing, with its dedicated Quality Assurance (QA) services, offers a reliable solution to identify potential vulnerabilities, detect security risks, and fortify your web and mobile applications against cyber threats.

Holistic Security Assessment:
Risk Mitigation Strategies:
Regulatory Compliance Assurance:
Incident Response Preparedness:
User Confidence and Brand Reputation:
Empowering your software to perform at its best






.webp)



.webp)







.webp)

We're all ears and eager to discuss your testing needs!
Crafting the best testing strategy for your product starts here.