Launching or managing a card program comes with great opportunities but also big responsibilities. One of the most important is ensuring the security of cardholder data. That’s where the Payment Card Industry Data Security Standard (PCI DSS) comes in.
Think of PCI DSS as a global rulebook for protecting sensitive payment information. Whether you’re a fintech startup, a bank, or a payment solution provider, meeting PCI DSS requirements is not just about compliance, it's about building trust and safeguarding your business against cyber threats.
In this blog, we’ll break down PCI DSS in simple terms and guide you through the essentials of compliance testing so your card program can launch smoothly and securely.
💡 What You’ll Learn in This Blog 📝
📌 What PCI DSS means and why it matters for card programs?
📌 Key objectives of PCI DSS, including protecting data and maintaining strong security practices.
📌 The compliance testing process, explained step by step.
📌 Essential services and tools that make PCI DSS compliance easier
📌 Best practices to follow when launching a card program with PCI DSS in mind.
What is PCI DSS?
The Payment Card Industry Data Security Standard (PCI DSS) is a globally recognized framework that outlines security requirements for businesses handling payment card transactions. It was developed by the Payment Card Industry Security Standards Council (PCI SSC) founded by major card brands like Visa, Mastercard, American Express, Discover, and JCB.

At its core, PCI DSS sets rules to ensure that cardholder data including account numbers, expiration dates, and security codes is kept safe from fraud, theft, and cyberattacks. Any organization that stores, processes, or transmits cardholder data must comply with these standards.
Why PCI DSS Compliance is Crucial for Card Programs
When launching or managing a card program, achieving PCI compliance is not just a regulatory requirement, it's a business necessity. The goal of the PCI Data Security Standards is to safeguard cardholder information, ensure secure credit card transactions, and minimize the risk of credit card fraud.
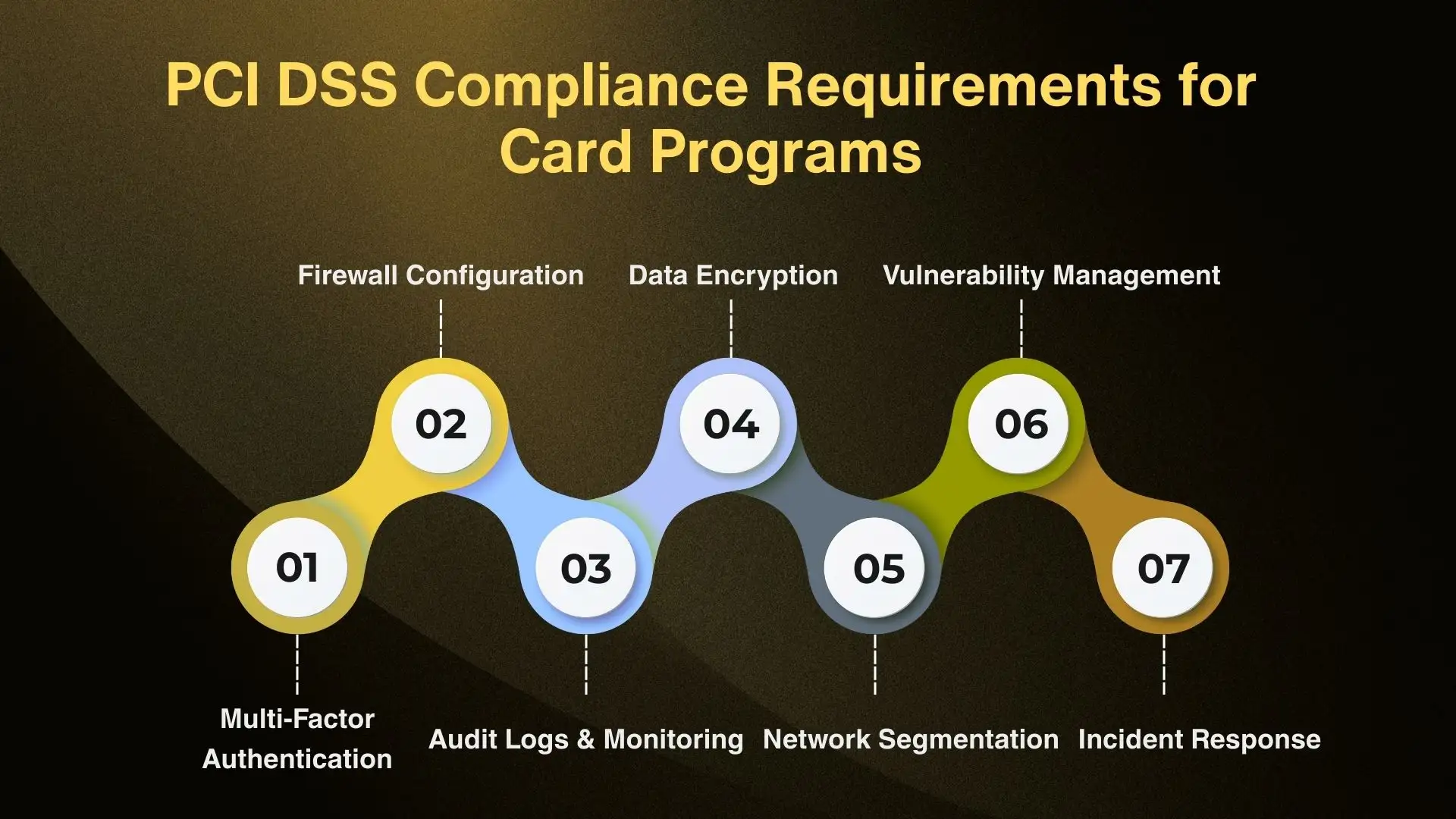
Here’s why compliance is essential:
- Protects Sensitive Data
PCI DSS helps prevent unauthorized access to credit card numbers, authentication data, and sensitive authentication data through strong security controls like firewall configuration, data encryption, and multi-factor authentication. - Prevents Data Breaches and Fraud
With regular Vulnerability Scans, penetration testing, and threat detection mechanisms, businesses reduce their exposure to security vulnerabilities that could result in costly security incidents or payment card fraud. - Builds Trust and Reputation
Customers and payment processors expect strong security solutions. Non-compliance can cause severe reputation damage, financial losses, and even the suspension of payment processing privileges. - Supports Regulatory Requirements
Meeting PCI DSS compliance checklist items ensures organizations align with payment processing guidelines and industry-wide control objectives, making them more resilient against evolving cyber threats. - Ensures Business Continuity
By implementing endpoint detection and response, cloud security tools, and proper user access controls for privileged users, organizations can maintain secure operations and avoid disruptions caused by security incidents.
Key Objectives of PCI DSS
The PCI Data Security Standards (PCI DSS) are built around a series of control objectives designed to strengthen payment processing systems, prevent data breaches, and secure cardholder information during credit card transactions. These objectives serve as the foundation for PCI compliance validation and ensure businesses adopt effective network security controls, security services, and security solutions.
Protect Cardholder Data
Cardholder data, including the Primary Account Number (PAN), cardholder name, and sensitive authentication data, is the main target of cybercriminals. Protecting this information is critical to preventing data breaches and credit card fraud.
Key Practices:
1. Data Encryption
- Use strong encryption protocols to secure cardholder data in storage and during transmission.
- Regularly update encryption keys and follow secure lifecycle management.
2. Data Minimization
- Store only essential cardholder data and establish clear data retention policies.
- Immediately delete data that no longer serves a business or compliance purpose.
3. Masking & Truncation
- Mask or truncate credit card numbers when full display is not necessary (e.g., showing only the last 4 digits).
4. Secure Transmission
- Ensure payment processors and third-party services use secure protocols (TLS/SSL).
- Avoid sending authentication data over unsecured channels like email.
Maintain a Secure Network
Payment environments are a prime target for attackers. Building a strong, layered network security framework helps block intrusions and reduce security vulnerabilities in payment processing systems.
Key Practices:
1. Firewall Configuration
- Define strict firewall policies to block unauthorized traffic.
- Regularly review and update configurations to align with evolving threat detection needs.
2. Network Segmentation
- Separate payment networks from general business networks to limit exposure.
- Use cloud security tools and endpoint detection and response (EDR) to strengthen protection.
3. Antivirus & Anti-malware
- Deploy and regularly update antivirus software.
- Automate scanning for malicious activity in both on-premises and cloud-based systems.
4. Patch Management
- Apply updates promptly to close known security vulnerabilities.
- Track patches across third-party software and services.
Implement Strong Access Control
Unauthorized access to systems handling credit card transactions is a major cause of security incidents. Strong access control ensures only privileged users with legitimate business needs can reach sensitive environments.
Key Practices:
1. Principle of Least Privilege
- Grant access only to user access levels necessary for job roles.
- Regularly audit access rights to remove unnecessary privileges.
2. Authentication Controls
- Enforce multi-factor authentication (MFA) for all users, especially administrators.
- Use secure authentication mechanisms instead of shared credentials.
3. User Accountability
- Assign unique IDs to each user for tracking actions.
- Monitor audit logs to detect unusual behavior.
4. Password Security
- Follow strict password policies (length, complexity, rotation).
- Avoid default credentials in third-party services.
Regularly Monitor and Test Security
Security is an ongoing process, not a one-time setup. Continuous monitoring and testing identify weaknesses early and protect against emerging threats in payment processing systems.
Key Practices:
1. Vulnerability Management
- Conduct quarterly Vulnerability Scans and annual penetration testing.
- Address findings quickly to minimize risk exposure.
2. System Monitoring
- Implement threat detection tools such as IDS/IPS.
- Use SIEM (Security Information and Event Management) for real-time monitoring of anomalies.
3. Audit & Logging
- Maintain detailed audit logs for all credit card payment activities.
- Regularly review logs for signs of suspicious activity.
4. Incident Response
- Develop a clear incident response plan to minimize damage from a breach.
- Train teams to handle events such as malware outbreaks or data leaks.
PCI DSS Compliance Testing Process
Achieving and maintaining PCI DSS certification requires more than just implementing security measures, it demands continuous security testing and validation. The PCI DSS compliance process ensures that every organization handling credit card transactions can protect sensitive cardholder information, prevent data breaches, and meet industry regulations.
Compliance testing is not just about passing an audit, it’s about building long-term trust with customers, credit card companies, and payment processors while reducing the risks of credit card fraud.
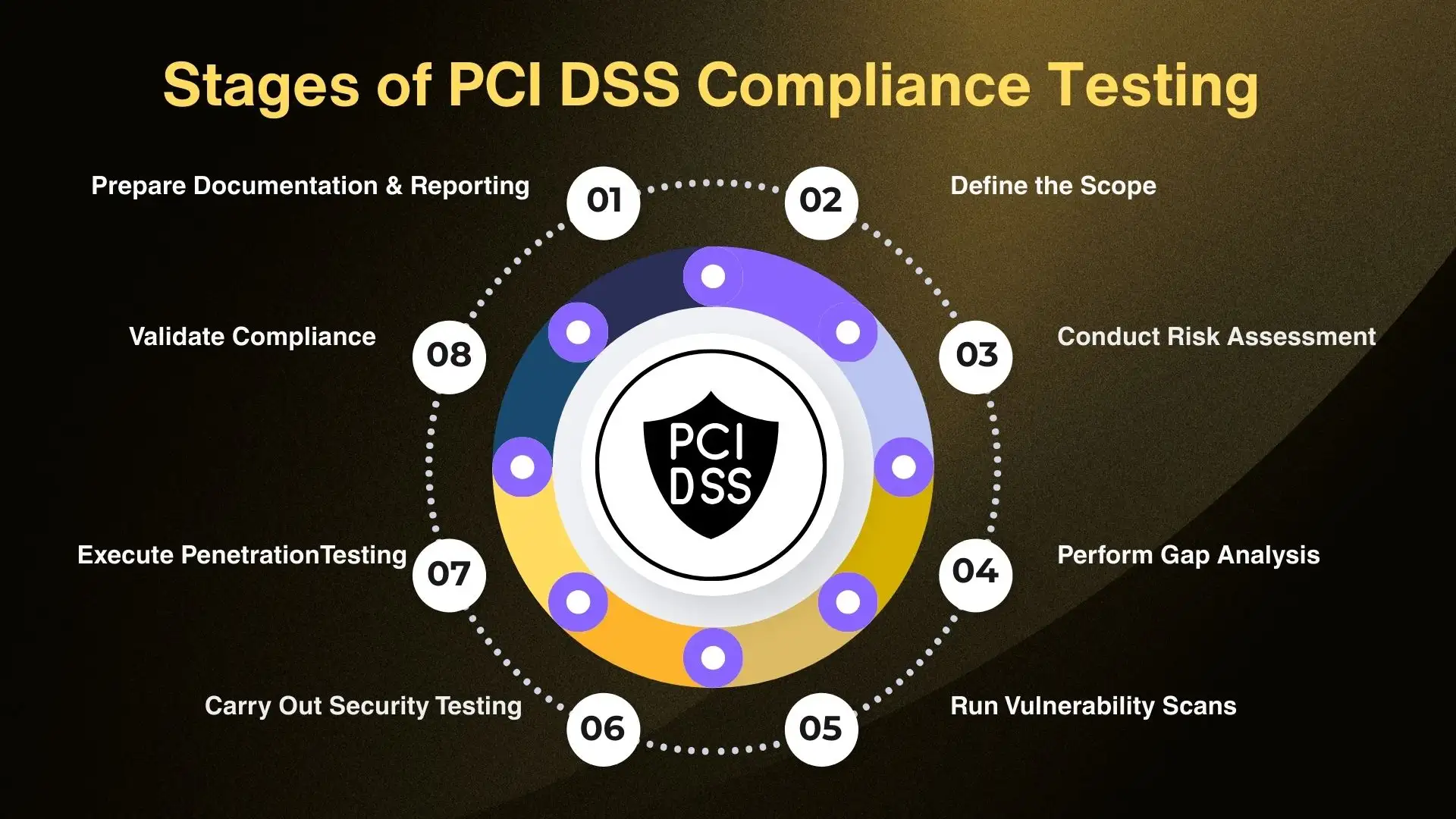
1. Define the Scope: Identify all systems, applications, networks, and third-party providers that store, process, or transmit cardholder data. Establish boundaries to determine what falls under the compliance review.
2. Conduct a Risk and Gap Assessment: Review current security policies, processes, and technical controls. Compare them against PCI DSS requirements to identify gaps. Assess risks that could lead to unauthorized access or data exposure.
3. Perform Vulnerability Scans and Security Testing: Run automated vulnerability scans on systems and applications. Test web, mobile, and cloud applications for weaknesses. Evaluate security configurations such as firewalls, antivirus, and data encryption.
4. Carry Out Penetration Testing: Simulate real-world cyberattacks to identify exploitable weaknesses. Test both internal and external environments. Validate the effectiveness of security measures such as network segmentation and authentication controls.
5. Validate Compliance and Document Findings: Compile evidence of implemented controls and security measures. Submit results for independent validation by a qualified assessor. Document compliance status and remediation steps for ongoing improvement.
Essential Services for PCI DSS Compliance
To meet PCI DSS compliance goals, organizations often need specialized services and expertise. These services not only help with achieving PCI DSS certification but also ensure continuous protection against evolving threats. Below are the key services that support the PCI DSS compliance process.

Qualified Security Assessor (QSA) Services
Qualified Security Assessors (QSAs) are certified by the PCI Security Standards Council to perform independent audits and validations. Their expertise ensures your organization is not just “checking the box” but truly securing cardholder information.
- Perform official PCI DSS assessments across systems, applications, and networks.
- Evaluate security controls like firewall configuration, encryption protocols, and access controls.
- Provide actionable guidance for closing gaps in compliance.
- Issue final validation reports that support PCI DSS certification.
- Assist in developing a long-term PCI DSS information security policy.
Approved Scanning Vendor (ASV) Services
ASVs are authorized to conduct mandatory vulnerability scans required by PCI DSS standards. These scans help uncover weaknesses in payment processing systems before they can be exploited by attackers.
- Run quarterly vulnerability scans to meet PCI DSS requirements.
- Focus on identifying security vulnerabilities in internet-facing systems.
- Cover areas like web application security testing, cloud security tools, and third-party software integrations.
- Provide official ASV compliance reports for inclusion in the PCI DSS compliance checklist.
- Recommend remediation steps for rapid issue resolution.
Third-Party Penetration Testing and Audit Services
While vulnerability scans highlight common issues, penetration testing dives deeper. Independent third-party testing ensures that your security incident response strategy is battle-tested against real-world threats.
- Simulate real-world cyberattacks using cyber security penetration testing techniques.
- Cover mobile app security testing, API security testing, and web app security testing.
- Validate key security controls such as multi-factor authentication, network segmentation, and encryption keys.
- Conduct compliance audits that map findings directly to PCI DSS compliance regulations.
- Provide detailed remediation and improvement roadmaps.
Managed Security Service Providers (MSSPs)
MSSPs act as long-term security partners for businesses, especially in the fintech industry, where fintech payment solutions demand high trust and security. They help organizations manage compliance continuously rather than treating it as a once-a-year audit.
- Deliver 24/7 monitoring, threat detection, and incident response.
- Integrate advanced solutions like endpoint detection and response (EDR) and cloud security tools.
- Provide continuous security testing services using automated and manual methods.
- Maintain updated audit logs and compliance documentation.
- Offer flexible PCI DSS compliance services to support growing payment processors and fintech payment gateways.
Popular PCI DSS Testing Tools
Maintaining PCI DSS compliance requires more than policies and paperwork, it demands rigorous security testing across every system that touches cardholder information. As organizations adopt fintech technology, cloud testing platforms, and complex payment processing systems, relying solely on manual checks isn’t enough.
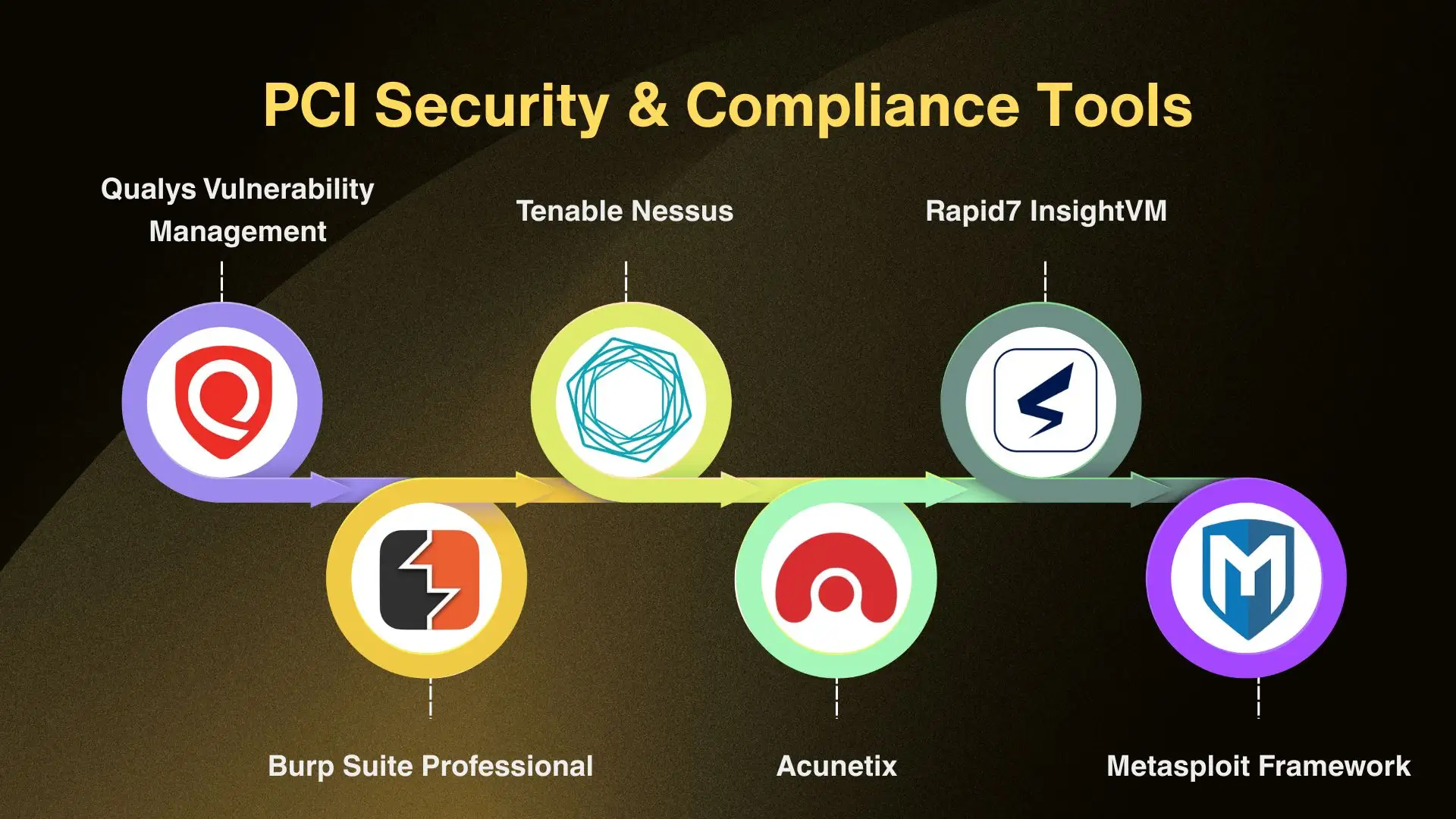
1. Qualys Vulnerability Management
A cloud-based PCI DSS services platform recognized by the PCI Security Standards Council. Ideal for ongoing vulnerability management across payment processing environments.
Key Features
- Automates PCI DSS compliance certification scans across servers, databases, and cloud assets.
- Generates ASV-approved reports for your PCI DSS documentation and audit logs.
- Maps findings directly to PCI DSS checklist items to simplify remediation tracking.
- Scales easily for large fintech payment solutions and third-party services.
2. Tenable Nessus
A trusted vulnerability scanning solution designed to help organizations strengthen network security controls and protect cardholder information.
Key Features
- Identifies missing patches, weak encryption protocols, and policy gaps affecting PCI DSS 4.0 requirements.
- Prioritizes threats by severity, helping teams secure critical payment processing systems first.
- Integrates with existing security testing services to streamline remediation.
- Offers detailed reports for compliance validation and ongoing risk assessments.
3. Rapid7 InsightVM
Modern software security testing for organizations seeking real-time insight into security posture and compliance readiness.
Key Features
- Live, agent-based scanning across on-prem, cloud, and hybrid payment processing environments.
- Risk scoring aligned to PCI DSS compliance goals and actionable remediation guidance.
- Tracks remediation progress against your PCI DSS checklist.
- Dashboards support auditors and PCI DSS assessment preparation.
4. Burp Suite Professional
An industry-favorite toolkit for web application security testing, especially for portals handling credit card numbers or sensitive authentication data.
Key Features
- Intercepts and analyzes HTTP/S traffic to detect SQL injection, XSS, and session issues.
- Supports manual and automated scanning for web app security testing.
- Integrates with CI/CD pipelines, reinforcing secure software frameworks during PCI DSS implementation.
- Generates detailed, developer-friendly vulnerability reports for quick fixes.
5. Acunetix
A powerful web security testing platform suited for scanning e-commerce, API endpoints, and fintech payment gateways.
Key Features
- Detects injection flaws, weak server configurations, and sensitive authentication data exposure.
- Performs authenticated scans to mimic real user interactions on credit card payments workflows.
- Exports detailed findings directly into PCI DSS documentation workflows.
- Helps meet PCI DSS compliance checklist requirements for application-level security.
6. Metasploit Framework
An advanced toolkit for pen testing cyber security, validating that implemented controls truly prevent credit card fraud.
Key Features
- Simulates real-world attacks to test firewall configuration, network segmentation, and multi-factor authentication.
- Verifies effectiveness of security solution deployments across cardholder data environments.
- Confirms remediation of previously identified vulnerabilities from Nessus, Qualys, or Rapid7 scans.
- Strengthens incident response planning for PCI DSS compliance certification.
Best Practices for PCI DSS Compliance in Card Program Launches
Launching a new card program demands strong safeguards for cardholder data. Building PCI DSS compliance into every stage reduces risk, supports smooth certification, and protects customer trust.
- Plan Early: Integrate PCI DSS 4.0 requirements into design and architecture from day one.
- Follow a Structured Checklist: Map each requirement to owners and milestones.
- Embed Secure Development: Apply static and dynamic application security testing throughout the SDLC.
- Run Regular Vulnerability Scans: Detect issues before they impact payment systems.
- Perform Penetration Testing: Simulate attacks to confirm security resilience.
- Maintain Robust Documentation: Keep policies, procedures, and test evidence audit-ready.
- Train Teams: Educate staff on secure cardholder data handling and compliance duties.
- Engage Trusted Experts: Leverage QSA, ASV, or managed PCI DSS services for specialized guidance.
- Monitor Continuously: Enable real-time alerts, log reviews, and periodic reassessments.
Conclusion
Achieving and maintaining PCI DSS compliance is not a one-time checkbox, it's an ongoing commitment to safeguarding cardholder data and preserving customer trust. By understanding what PCI DSS stands for, aligning with its key objectives, and following a structured compliance testing process, organizations can build stronger, more secure card programs.
Leveraging essential services such as QSA assessments, ASV scanning, third-party penetration testing, and managed security providers ensures that every layer of the payment environment is evaluated and protected. Modern testing tools like Qualys, Nessus, Rapid7, Burp Suite, and Acunetix combined with AI-driven test automation services and cloud-based test automation services help identify vulnerabilities and streamline repetitive tasks, keeping compliance agile and efficient. Partnering with QA testing services for enterprises further strengthens governance and documentation across large card portfolios.
Working alongside experienced software testing companies and incorporating load testing services validates system resilience under high-volume transactions, helping operators prepare for real-world conditions.
For card program operators and fintech businesses, PCI DSS compliance is both a regulatory requirement and a competitive advantage. Embedding security into every stage of implementation not only supports certification but also strengthens resilience against evolving cyber risks, enabling growth with confidence.
FAQs
1. What is the impact of PCI DSS 4.0 on new card program launches?
PCI DSS 4.0 raises the bar with tighter controls, flexible validation methods, and an emphasis on continuous risk management. Teams need early planning for multi-factor authentication, stronger encryption, and regular vulnerability oversight.
2. How can early PCI DSS testing reduce delays in card program go-live?
By identifying security gaps well before certification, early testing prevents last-minute fixes and keeps the launch schedule on track. It turns compliance into a planned activity instead of a rushed deadline task.
3. How do banks and fintechs ensure continuous PCI DSS compliance after a card launch?
They schedule regular vulnerability scans, penetration tests, and keep PCI DSS documentation current. Many partner with Managed Security Service Providers (MSSPs) for 24/7 monitoring and rapid incident response.
4. Does PCI DSS compliance differ for debit, credit, and prepaid card programs?
The core requirements are the same across all card types. Minor differences appear only in how cardholder data is processed and stored, not in the underlying PCI DSS standards.
5. What is the role of tokenization and encryption in PCI DSS compliance for new cards?
Tokenization replaces real card numbers with secure tokens, while encryption protects cardholder data in transit and at rest. Together, they reduce PCI DSS scope and enhance payment security.




%201.webp)