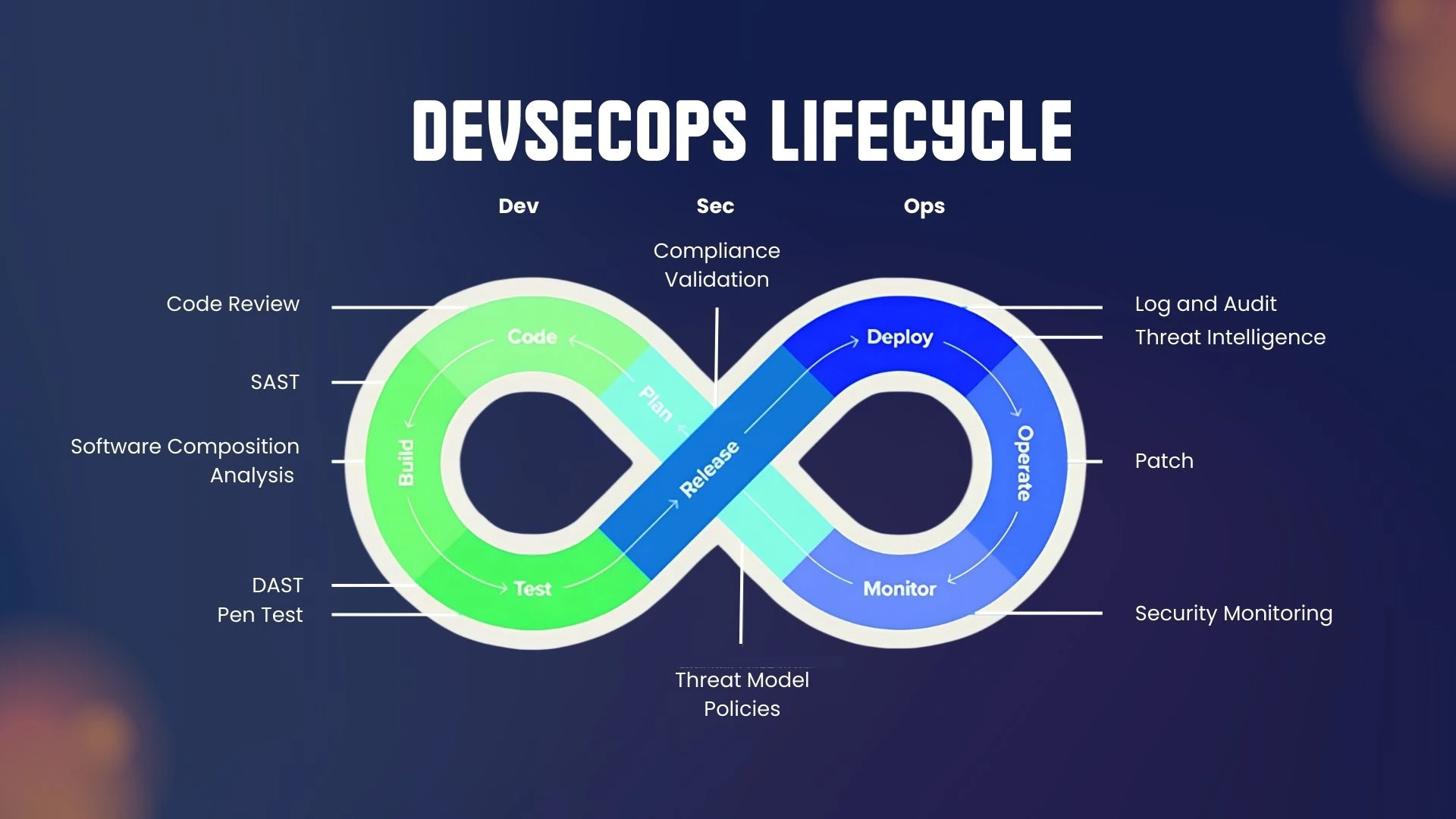
With the complexity of modern software systems, DevSecOps has become essential for embedding security across every stage of the CI/CD pipeline. In 2025, adopting the right DevSecOps tools ensures continuous, automated security checks without slowing down innovation. These tools cover everything from static code analysis, container scanning, secrets management, artifact security, and even network mapping through techniques like nmap scan to identify potential attack surfaces.
This guide explores the top 10 DevSecOps tools for 2025: Snyk, Aikido Security, Checkmarx, Aqua Security, Tenable, Trivy, GitGuardian, JFrog Xray, SonarQube, and OWASP ZAP. Together, these tools balance speed and security by providing real-time monitoring, vulnerability detection, and compliance enforcement.
What you’ll discover:
- How each tool addresses a unique part of the DevSecOps ecosystem
- Features that make these tools essential for 2025
- How practices like nmap scan complement DevSecOps for complete security coverage
- Best practices for integrating these tools seamlessly into your CI/CD pipeline
- How to choose the right combination of tools based on your enterprise security needs
What is DevSecOps and Why It Matters
DevSecOps stands for Development, Security, and Operations, a methodology integrating security as a shared responsibility throughout the software development lifecycle (SDLC).
Why DevSecOps matters in 2025?
📌 Reduces vulnerabilities early in the SDLC
📌 Promotes developer involvement in security
📌 Automates scans across CI/CD pipelines
📌 Cuts remediation costs and improves compliance
📌 Enables faster and safer software delivery
Traditional security tools focus only on post-deployment validation. In contrast, DevSecOps integrates shift-left practices, where security checks (including container scans, IaC scanning, and even basic nmap scan for network visibility) happen from the first line of code.
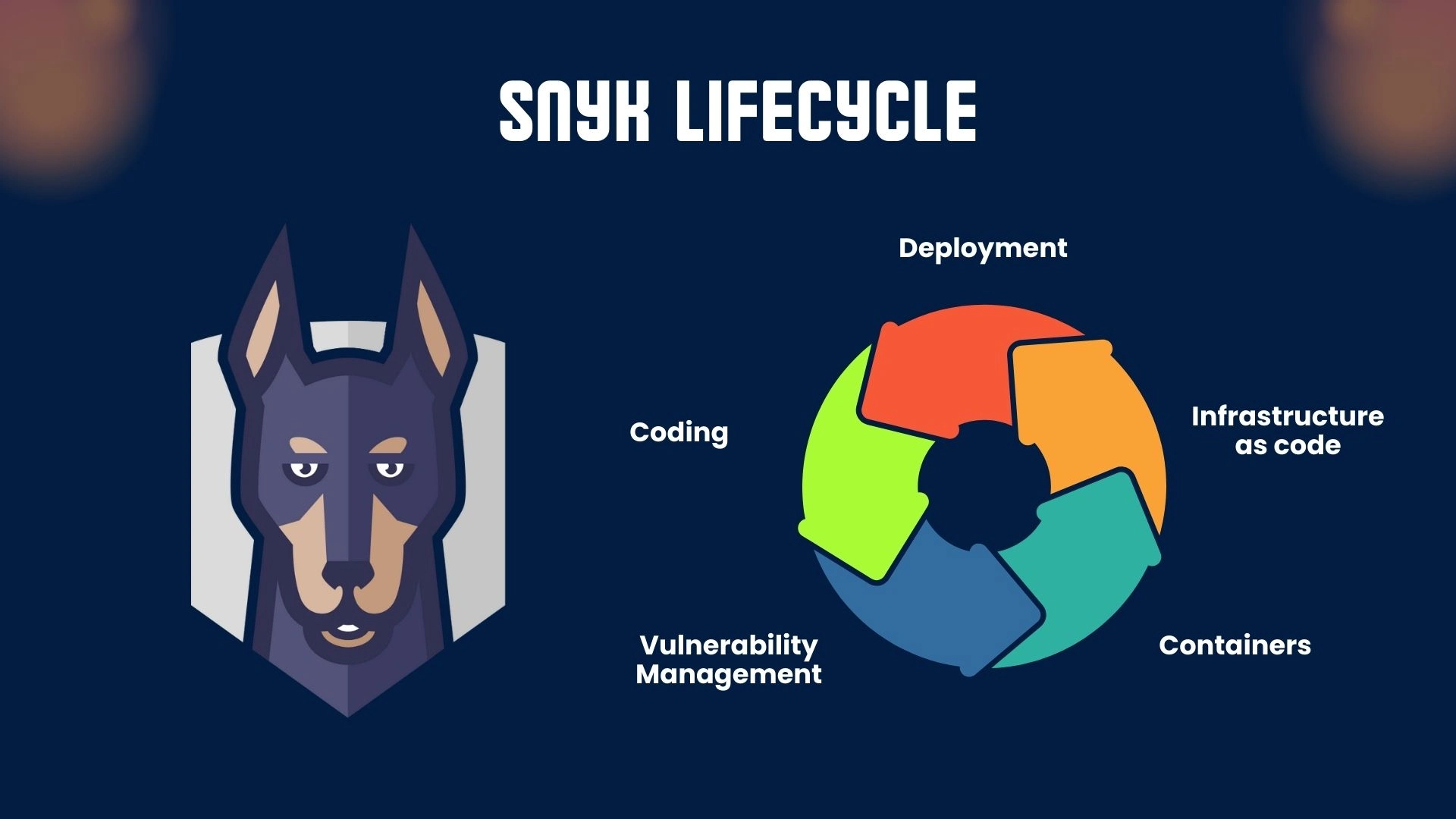
Snyk – Open Source Security for Developers
Snyk empowers developers to build securely by detecting and fixing vulnerabilities in open source packages, containers, and Infrastructure as Code (IaC). Unlike traditional tools that rely solely on post-deployment scans, Snyk integrates seamlessly into the developer workflow, allowing issues to be identified directly within IDEs or during pull requests.
Its extensive language support (Java, JavaScript, Python, Go, and more) makes it suitable for diverse tech stacks, while its automated remediation capabilities reduce manual effort through fix suggestions and pre-built patches.
Key Highlights:
- Real-time scanning with automated fixes
- Supports Java, JavaScript, Python, Go, and more
- Integrates with GitHub, GitLab, Bitbucket, Jenkins
- Visual IDE plugin and Git-based PRs for fixes
- Popular for DevOps teams exploring Snyk pricing, Snyk logo, Snyk careers
Use Case: Perfect for shift-left security in containerized microservices. Teams often pair Snyk scans with nmap scan to identify external network exposure post-deployment..
Aikido Security – Fast, Automated Threat Detection
Aikido Security focuses on real-time vulnerability detection with minimal noise, making it ideal for agile teams working in fast-paced environments. Unlike traditional scanners that generate excessive alerts, Aikido uses smart prioritization to highlight the most critical issues first, reducing alert fatigue. It supports detection of CVEs, misconfigurations, and secrets in code, containers, and Infrastructure as Code (IaC).
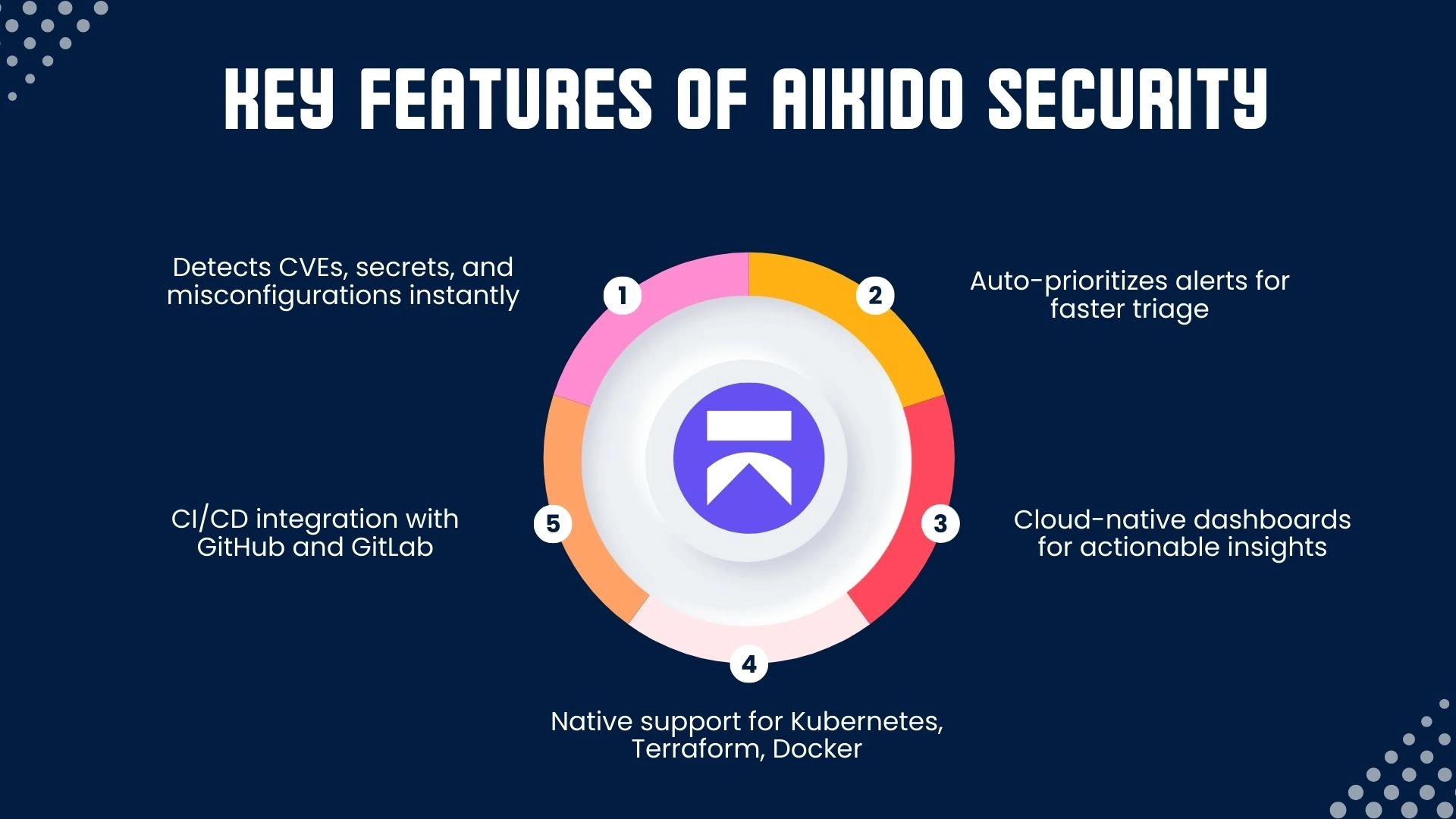
Use Case: Great for fast-paced teams. Combining Aikido with nmap scan provides holistic visibility: Aikido covers code and containers, while nmap maps live network surfaces.
Checkmarx – Static Code Analysis with High Accuracy
Checkmarx is a leader in Static Application Security Testing (SAST), enabling developers to detect vulnerabilities early in the coding phase before they progress into later stages of the software development lifecycle.
It provides deep insights into security flaws with context-aware scanning that reduces false positives, ensuring developers can focus on the most critical issues. Checkmarx supports over 25 programming languages and frameworks, making it highly versatile for enterprise environments.
Top Benefits:
- Supports 25+ languages and frameworks
- AI-powered context-aware scanning
- CI/CD, IDE, and ticketing system integration
- Compliance and governance reporting
Use Case: Enterprises use Checkmarx for code hygiene and compliance. After scanning source code, a nmap scan complements it by validating exposed ports in staging environments.
Aqua Security – End-to-End Cloud-Native Protection
Aqua Security provides comprehensive cloud security for containers, serverless functions, and virtual machines across the entire cloud environment and cloud infrastructure. It integrates Runtime Security Tools, Compliance automation, and cloud security posture management to strengthen security practices and reduce the risk of a security breach.
By combining image scanning, runtime protection, API security, and Vulnerability assessment, Aqua ensures robust security orchestration and proactive Incident Response across modern DevSecOps workflows.
Aqua continuously monitors workloads at runtime to prevent drift, mitigate security risks, and automate security tasks across hybrid and multi-cloud environments. It enables teams to enforce security practices while ensuring compliance, forensics, and seamless Incident Response during potential threats.
Capabilities include:
- Aqua container security for image scanning, Vulnerability assessment, and policy enforcement.
- Aqua cloud security for IAM, runtime protection, API security, and Runtime Security Tools.
- Aqua security software for Compliance automation, forensics, and security risk management.
- Prevents drift in Kubernetes and orchestrated environments with cloud security posture management and security orchestration.
- Visual dashboards for threat insights and automated security tasks.
Use Case: Ideal for DevOps teams running Kubernetes and multi-cloud deployments, ensuring API security, cloud protection, and incident response to maintain a strong cloud security posture.
Tenable – Comprehensive Vulnerability Management
Tenable delivers broad vulnerability management across on-premises, cloud, and hybrid infrastructures. It is best known for its Tenable Nessus scanner, which identifies and prioritizes vulnerabilities with precision. Tenable provides real-time asset discovery, risk-based scoring, and integrations that make it suitable for enterprise security operations and DevSecOps pipelines alike.
Why Tenable excels:
- Asset discovery for cloud, on-prem, hybrid
- Risk-based prioritization with actionable metrics
- DevOps-friendly CI/CD plugins
- Enterprise confidence backed by Tenable stock strength
Use Case: Tenable secures hybrid infrastructures by scanning cloud, container, and on-prem assets, integrating into CI/CD for automated risk assessments and regulatory compliance.
Trivy – Lightweight Vulnerability Scanner for Containers
Trivy by Aqua is a simple yet powerful tool designed to scan containers, IaC configurations, and Kubernetes clusters for vulnerabilities. As an open-source solution, it is widely adopted for its speed and ease of use. Trivy performs comprehensive checks on operating system packages, application dependencies, and misconfigurations, making it an essential part of DevSecOps workflows focused on container security.
Key advantages:
- Trivy scan CLI for fast vulnerability checks
- Supports container images, IaC, and GitOps
- Trivy operator scans live Kubernetes workloads
- Integrated with GitHub, GitLab, Jenkins
- Part of Aqua Trivy open source suite
Use Case: Trivy helps container-first teams secure images, IaC, and Kubernetes clusters by integrating scans into CI/CD pipelines. With trivy scan for builds and Trivy Operator for runtime, it ensures consistent security across Dev, GitOps, and production.
GitGuardian – Secrets Detection Made Easy
GitGuardian helps organizations prevent credential leaks by detecting secrets in both public and private repositories. It continuously scans commits, branches, and pull requests to identify API keys, passwords, and other sensitive data that may have been accidentally exposed. Designed for developer-first adoption, GitGuardian integrates seamlessly with modern development platforms to provide instant feedback and remediation guidance.
- Real-time alerting on secret exposure
- Integrates into GitHub, GitLab, Bitbucket
- Tracks incidents and remediation progress
- Machine learning reduces false positives
- Scans CI/CD logs, IaC, Dockerfiles
Use Case: GitGuardian is ideal for teams aiming to prevent secret leaks by scanning repositories, CI/CD logs, and Dockerfiles in real time. It blocks sensitive data like API keys and passwords from reaching production while providing instant alerts and remediation workflows. Integrated with GitHub, GitLab, and Bitbucket, it ensures secrets management across the entire DevSecOps pipeline.
JFrog Xray – DevSecOps Intelligence for Artifacts and Containers
JFrog Xray provides deep visibility into artifacts, binaries, and containers across the software supply chain. It performs advanced scanning to identify vulnerabilities, license compliance issues, and malicious packages before they impact production. Integrated tightly with JFrog Artifactory, Xray ensures that every component entering your CI/CD pipeline is verified for security and compliance
Top features:
- Deep dependency and license scanning
- Native integration with JFrog Artifactory
- CI/CD plugin compatibility (GitHub, Jenkins, Azure DevOps)
- Policy-driven artifact blocking
- Real-time threat intelligence feeds
Use Case: JFrog Xray secures the software supply chain by scanning artifacts, binaries, and containers for vulnerabilities and license risks, blocking unsafe components via CI/CD and Artifactory integration.
SonarQube – Code Quality and Security in One Platform
SonarQube is a comprehensive platform designed to ensure that code is not only secure but also maintainable and compliant with industry standards. It performs static code analysis to identify bugs, vulnerabilities, and code smells across multiple programming languages, empowering teams to improve software quality early in the development lifecycle.
By integrating directly into CI/CD pipelines, SonarQube provides continuous feedback, helping developers address issues before they reach production.
Why developers love it:
- Static analysis to detect bugs, smells, and vulnerabilities
- Coverage across 30+ languages
- Seamless setup with Jenkins, GitHub Actions
- Available as community, developer, and enterprise editions
Common queries answered:
- What is SonarQube?
An open-source platform for static code analysis that improves software quality by detecting bugs and vulnerabilities. - SonarQube Download:
Available from the official SonarQube website. - What is SonarQube Used For?
To integrate code quality checks into CI/CD pipelines, reduce technical debt, and ensure clean, secure, and maintainable code.
Use Case: Dev teams looking to standardize secure coding practices and reduce technical debt.
OWASP ZAP – Free, Powerful Dynamic Application Security Testing
OWASP ZAP (Zed Attack Proxy) is one of the most popular open-source Dynamic Application Security Testing (DAST) tools. It simulates attacker behavior to identify vulnerabilities in live applications, making it ideal for testing runtime issues such as cross-site scripting (XSS), SQL injection, and insecure configurations that static tools might miss. With its intuitive interface and automation-friendly design, OWASP ZAP is suitable for both beginners and advanced security teams.
Tool Highlights:
- Ideal for testing live web and mobile applications.
- Detects runtime flaws including XSS, SQLi, and insecure cookies.
- Seamlessly integrates with CI/CD pipelines for scheduled scans.
- Extensible through plugins and APIs, enabling customized workflows.
- Highly searched for terms like OWASP ZAP tool, OWASP ZAP download, and Zap OWASP, reflecting its global adoption.
Use Case: OWASP ZAP enables QA and security teams to automate dynamic scans within CI/CD pipelines, detect runtime vulnerabilities, and complement testing with manual and API-driven exploration. Its flexibility and ease of use make it a go-to choice for organizations adopting DevSecOps practices.
DevSecOps Best Practices to Maximize Tool Efficiency
Maximizing the value of DevSecOps tools requires strategic implementation and continuous improvement. These best practices help teams integrate security seamlessly into their workflows, ensuring robust protection without slowing down delivery.
Incorporating software composition analysis, enforcing security policies, and adapting to evolving cloud environments are essential for building a strong DevSecOps foundation.
Key strategies include:
- Shift security left: Embed testing early in the software development lifecycle, using tools like Snyk, Checkmarx, and SonarQube to identify vulnerabilities at the code level.
- Automate wherever possible: Integrate solutions such as OWASP ZAP and Trivy into CI/CD pipelines for consistent, hands-free scanning of applications, containers, and infrastructure.
- Contextualize alerts: Reduce noise by prioritizing high-impact vulnerabilities with tools like Aikido Security and Tenable, ensuring teams focus on critical issues first.
- Enforce security policies and access controls: Use GitGuardian for secrets detection and JFrog Xray for artifact compliance to prevent security drift and maintain governance across cloud environments.
- Continuously monitor production: Combine runtime protection from Aqua Security with network insights from nmap scan to ensure ongoing visibility into threats across cloud and on-prem environments.
Use Case: These practices unify tools, enhance collaboration, and enable continuous testing, using layered defenses like SAST, DAST, IaC scanning, and secrets management to build a resilient DevSecOps ecosystem.

Conclusion: Future-Proof Your CI/CD Pipeline with DevSecOps
In 2025, DevSecOps has evolved from an option to a necessity for building secure, scalable, and compliant CI/CD pipelines. By integrating security at every stage of the software development lifecycle, organizations can detect vulnerabilities early, minimize risks, and maintain compliance without slowing delivery.
The top tools - Snyk, Aikido Security, Checkmarx, Aqua Security, Tenable, Trivy, GitGuardian, JFrog Xray, SonarQube, and OWASP ZAP cover critical aspects of application and infrastructure security, from static and dynamic analysis to container scanning, secrets detection, and artifact intelligence. When used together, they create a layered defense that protects code, containers, and supply chains.
To future-proof your pipeline, shift security left, automate testing, manage secrets and artifacts, and enhance visibility with runtime and network-level monitoring. By embedding DevSecOps as a shared responsibility, teams can deliver software that’s not only faster but also resilient against evolving threats.
Frequently Asked Questions (FAQs)
👉What are the popular CI/CD tools in 2025?
Tools like Jenkins, GitHub Actions, GitLab CI/CD, and Azure DevOps are widely used for CI/CD automation, offering integrations with security tools to enable DevSecOps practices.
👉Which best security practice should be introduced to the CI/CD pipeline?
Integrate security early, automate scans, enforce policies, and continuously monitor post-deployment environments to ensure vulnerabilities are detected and resolved before they impact production..
👉What is the difference between CI/CD and DevSecOps?
CI/CD focuses on automating code integration, testing, and delivery, whereas DevSecOps integrates security into every stage of the CI/CD pipeline to ensure secure, compliant, and reliable software delivery.
👉Which tools are commonly used for automating CI/CD pipelines?
Tools like Jenkins, GitHub Actions, GitLab CI/CD, and Azure DevOps are widely used for CI/CD automation, providing seamless integrations with testing, monitoring, and security tools to support DevSecOps workflows..
👉What are the three pillars of DevSecOps?
- Automation – Integrating security checks automatically throughout the CI/CD pipeline.
- Collaboration – Promoting shared responsibility for security across development, operations, and security teams.
- Continuous Monitoring – Maintaining visibility, detecting threats, and ensuring compliance in real time.




%201.webp)