Creating a security testing plan is crucial for safeguarding applications, systems, and data against ever-evolving cyber threats. In 2025, with cybersecurity compliance standards and increasing digital reliance, organizations must follow a structured approach to ensure data protection and risk mitigation.
This comprehensive guide helps you uncover vulnerabilities, select the right security testing services, make use of penetration testing and static analysis security testing, and implement effective cybersecurity strategies. Whether you're focused on vulnerability scanning tools or ensuring continuous data protection, this plan will help build resilient, compliant, and secure software environments.

💡What’s Next? Keep reading to discover:
🚀 Why security testing is critical in today’s cybersecurity strategy
🚀 Key elements and structure of an effective security testing plan
🚀 A step-by-step walkthrough of planning and executing security tests
🚀 Ways to measure the success and effectiveness of your testing efforts
🚀 Common testing challenges and how to overcome them efficiently
Security Testing Plan Template: An Introduction
A security testing plan is a structured document that outlines how an organization will identify, test, and fix potential vulnerabilities in its applications, systems, and networks. It serves as a roadmap to protect digital assets from cyber threats by detailing testing objectives, scope, tools, techniques, and responsibilities to support effective cybersecurity risk management.
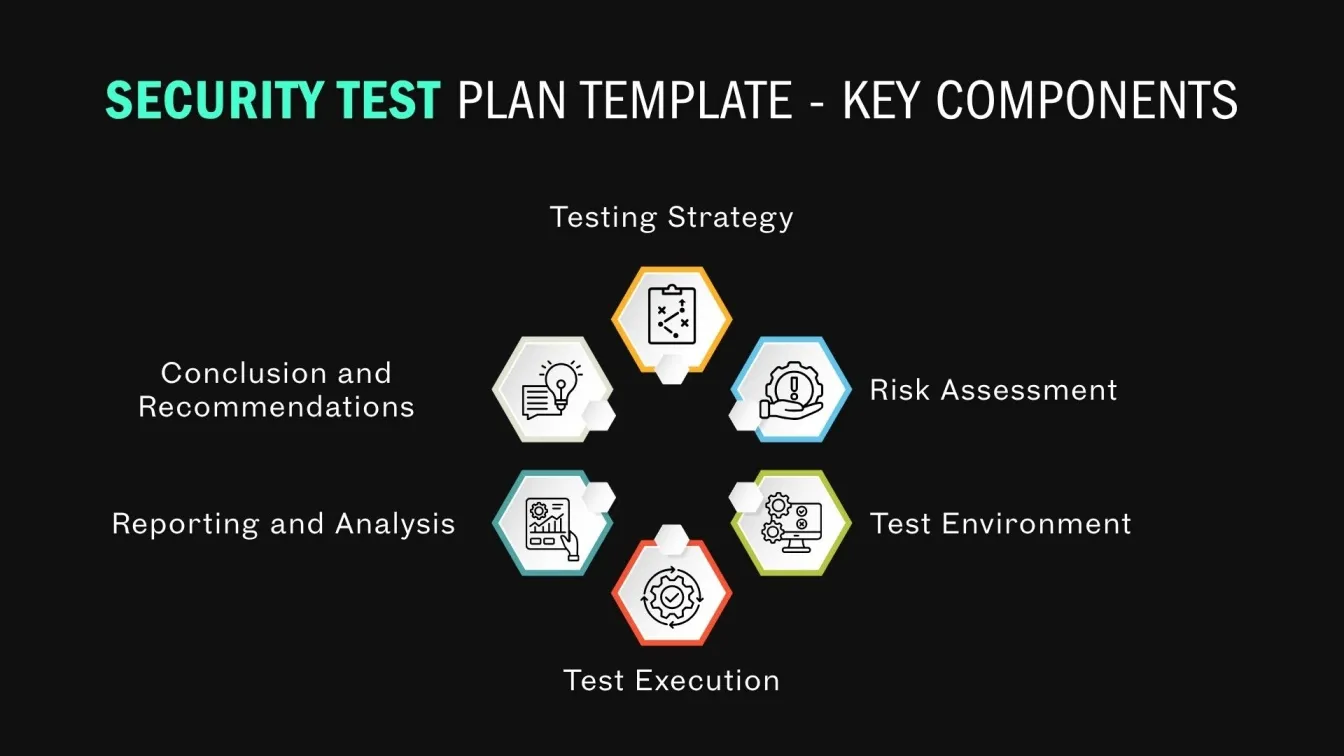
In 2025, with stricter data protection laws and growing digital dependencies, this plan helps ensure compliance with standards like GDPR, prevents data breaches, and improves incident response. It also defines the types of tests (e.g., penetration testing, vulnerability scanning, static code analysis), outlines risk-based prioritization, and guides teams in maintaining secure, reliable, and compliant software environments.
Importance of Security Testing in a Cybersecurity Strategy
Integrating security testing into your broader cybersecurity technology is a critical step toward building a secure digital foundation. With increasing threats and strict cybersecurity requirements, organizations can no longer rely solely on firewalls or antivirus software. Instead, a proactive and well-structured security testing approach is essential for reducing risks and meeting compliance standards.
- Early vulnerability detection: Security testing helps identify threats early using techniques like vulnerability scanning, penetration testing, and static analysis security testing, so teams can address weaknesses before they’re exploited.
- Ensures data protection and privacy: It safeguards sensitive information and aligns with data protection policies, including the General Data Protection Regulation (GDPR), ensuring user data privacy and system integrity.
- Supports cybersecurity compliance: Regular testing ensures your systems meet cybersecurity compliance benchmarks and follow industry-specific regulations and cybersecurity best practices.
- Builds stakeholder trust: Demonstrating security measures boosts confidence among users, clients, and stakeholders by showing your commitment to cyber threat protection.
- Strengthens incident response: A thorough security testing plan improves your ability to detect, respond to, and recover from security incidents quickly and effectively.
Real-World Security Flaws Exposed by Testing
Effective security testing is essential for identifying real-world vulnerabilities that put systems at risk. These hidden flaws often go undetected in live production environments, yet they pose serious threats to data integrity, system availability, and cybersecurity compliance.
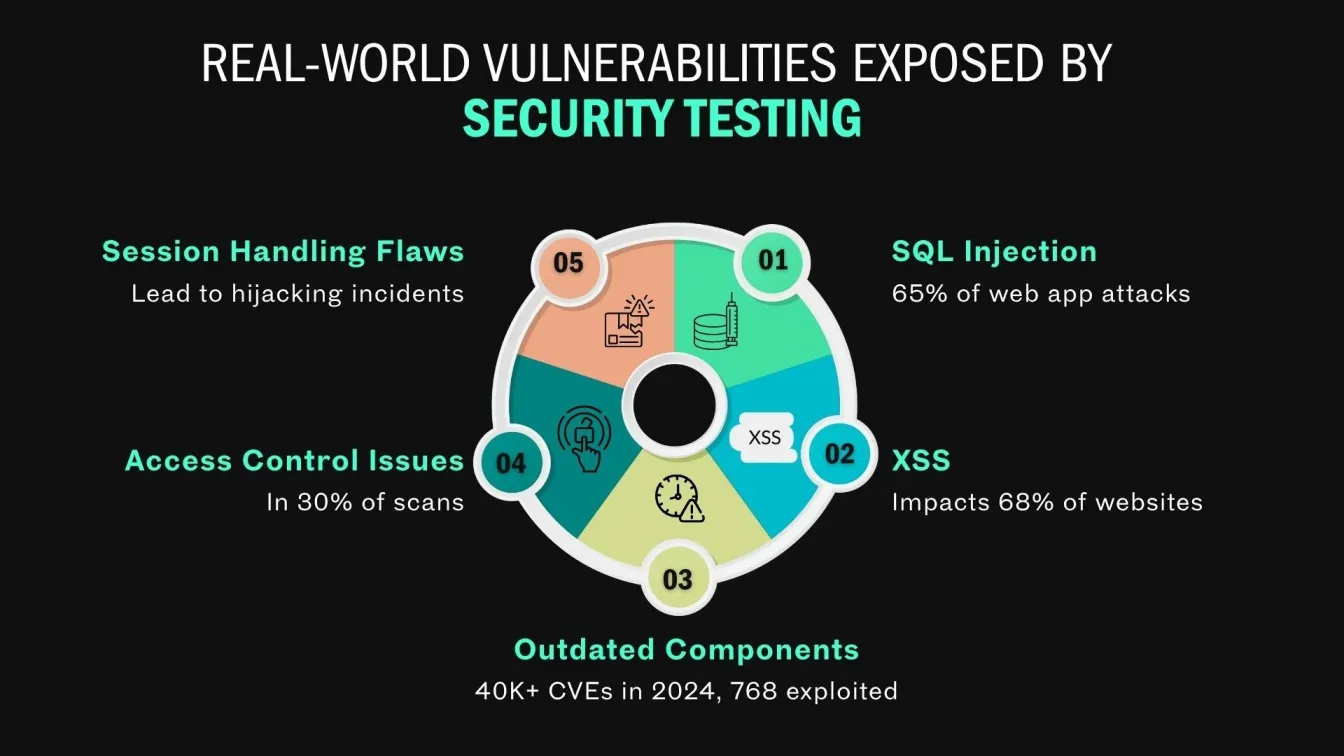
Common vulnerabilities uncovered through testing include:
- Injection Attacks (e.g., SQL or Command Injection): Enable attackers to alter backend queries or execute unauthorized commands.
- Cross-Site Scripting (XSS): Allows malicious scripts to run within trusted websites, potentially leading to stolen credentials or hijacked sessions.
- Exposed APIs and Endpoints: Weak access controls can reveal sensitive data or permit unauthorized interaction with backend systems.
- Insecure Session Management: Improper handling of tokens, cookies, or session IDs may allow attackers to take over user sessions.
- Outdated Components: Use of unpatched libraries or plugins containing known CVEs introduces exploitable vulnerabilities.
- Improper Access Controls: Inadequate permission settings can let users perform actions beyond their authorized roles.
- Unvalidated Inputs: Accepting unchecked input can result in buffer overflows, logic flaws, or denial-of-service conditions.
Step-by-Step Security Testing Plan Template
Creating a well-structured security testing plan is essential for ensuring application integrity, regulatory compliance, and overall cyber threat protection. In 2025, the increasing complexity of digital ecosystems demands a more detailed, step-by-step approach. This section outlines a practical and actionable security testing service roadmap, from identifying requirements to validating fixes, to help organizations stay resilient and secure.
Step 1: Identify Security Requirements
This initial step sets the foundation for your entire security testing plan. It involves identifying what needs protection, understanding the value of each asset, and determining relevant compliance needs.

Key Actions:
- Identify all business-critical assets servers, databases, APIs, web/mobile applications, network devices, and cloud environments.
- Define internal cybersecurity requirements and understand external regulations such as GDPR, HIPAA, and ISO 27001.
- Engage stakeholders from IT, development, DevOps, compliance, and legal teams to align business and security priorities.
- Determine system boundaries, data flow, access control levels, and potential threats or misuse scenarios.
Outcome:
A well-organized list of security priorities, mapped to applicable data protection solutions, business goals, and cybersecurity compliance standards, ensures your software security testing is well-aligned and focused from the start.
Step 2: Define Test Objectives and Scope
Defining your objectives and scope helps avoid wasted efforts, ensures strategic alignment, and focuses on what matters for your organization’s security posture.
Key Actions:
- Define specific goals: Detect vulnerabilities, verify encryption implementation, evaluate incident response readiness, or ensure data protection and privacy.
- Determine test scope: Should the test cover the entire application, just APIs, databases, or third-party integrations?
- Consider compliance requirements and integration points (e.g., API testing, external cloud services).
- Prioritize areas with known high risk or regulatory sensitivity.
Outcome:
A tightly scoped and clearly defined security testing plan that aligns with both technical and business objectives while maximizing the efficiency of cybersecurity service.
Step 3: Conduct Risk Assessment and Prioritization
Once the objectives and scope are clearly defined, the next critical step is to assess risks across your application's architecture. Risk assessment ensures testing efforts focus on the most vulnerable and business-critical areas.
Key Actions:
- Identify high-risk components such as APIs, user authentication systems, and payment modules.
- Use threat modeling or a risk matrix to evaluate the likelihood and impact of attacks.
- Prioritize assets storing sensitive data or enabling core functions.
- Align your prioritization with standards such as ISO 27001, OWASP ASVS, or NIST.
Outcome:
A clear, risk-based testing focus that ensures efficient use of testing resources while improving your application’s overall security posture.
Step 4: Choose Security Testing Types
Choosing the right mix of testing types ensures broad coverage and effective detection of different types of security weaknesses.
Key Actions:
- Select from a variety of security testing methods based on system architecture:
- Static Analysis Security Testing (SAST) – Examines code for flaws during development.
- Dynamic Analysis Security Testing (DAST) – Tests running applications for vulnerabilities.
- Penetration Testing – Simulates real-world attacks to uncover deeper issues.
- Vulnerability Scanning – Uses vulnerability scanning software or tools to detect known issues automatically.
- For cloud and third-party components, consider security and penetration testing software using sandbox environments.
Outcome:
An effective testing strategy that uncovers a wide range of threats, code-level flaws, configuration errors, and architectural weaknesses, aligned with your overall cybersecurity strategy.
Step 5: Select Tools and Prepare Test Data
Ensure your test execution is accurate, efficient, and compliant by selecting the right tools and preparing representative test data.
Key Actions:
- Choose suitable tools for security testing, commercial or open-source, based on scalability, reporting, compatibility, and automation needs.
- Examples: OWASP ZAP, Burp Suite, Nessus, SonarQube, or enterprise solutions like Fortify and Qualys.
- Create test data that mimics real-world inputs without violating data protection laws.
- Ensure test environments are isolated and mimic production setups closely for accurate results.
Outcome:
A test-ready setup that maintains regulatory and cybersecurity compliance while providing realistic, high-quality test outputs, paving the way for successful software security testing execution.
Step 6: Execute Security Tests
This step involves running the tests to detect known and unknown vulnerabilities within the defined scope.
Key Actions:
- Launch the testing phase using selected tools and methods across web apps, APIs, databases, or cloud environments.
- Monitor all activities and maintain logs for each test scenario.
- Collaborate with developers, DevSecOps, and QA teams for technical alignment.
- Focus on high-priority areas based on your earlier risk mapping.
Outcome:
A complete set of real-time test results identifying vulnerabilities, misconfigurations, and potential threat exposures. This phase provides a snapshot of your system’s security.
Step 7: Analyze Results and Report Vulnerabilities
Convert raw test data into actionable insights and ensure proper documentation and communication of findings.
Key Actions:
- Review logs, reports, and dashboard outputs to categorize vulnerabilities by type and severity.
- Link each vulnerability to potential business risks and compliance violations.
- Prepare a detailed report including:
- Vulnerability description
- Severity level and potential impact
- Affected systems or components
- Recommended mitigation or remediation steps
- Relevance to regulatory frameworks like GDPR, PCI-DSS, etc.
Outcome:
A well-structured vulnerability report that enables developers and leadership to prioritize and resolve security issues effectively, while maintaining cybersecurity compliance and risk management standards.
Step 8: Retesting and Final Validation
Ensure all vulnerabilities have been fixed and confirm that your environment is secure and compliant for deployment or production use.
Key Actions:
- Conduct retesting on previously identified vulnerabilities after applying patches or fixes.
- Perform additional penetration testing services or vulnerability scanning to validate data integrity.
- Compare the results with the original reports to ensure that no residual issues remain.
- Finalize documentation for audits and internal reviews.
Outcome:
A verified, secure, and compliant system that’s ready for production, meeting both technical expectations and cybersecurity requirements, with full confidence in your security testing services and testing framework.
Measuring the Effectiveness of Your Security Testing Plan
An effective security testing plan doesn’t stop at identifying vulnerabilities; it must demonstrate tangible improvements to your system’s security posture over time. By using key metrics and formulas, organizations can quantify the value and success of their testing efforts.
Key Metrics to Measure Effectiveness:
1. Vulnerability Detection Rate: Measures how many actual vulnerabilities your security tests successfully uncover.
Why it matters: A high detection rate shows that your test coverage is strong and that real threats are being identified before they reach production.
Detection Rate = (Number of Detected Vulnerabilities ÷ Total Known Vulnerabilities) × 1002. Time to Detect and Resolve: Measures how long it takes to detect a vulnerability after it's introduced, and how long it takes to fix it once found.
Why it matters: Faster detection and resolution reduce the exposure window, limiting the opportunity for attackers to exploit vulnerabilities.
Time to Detect (TTD) = Detection Time - Introduction Time
Time to Resolve (TTR) = Resolution Time - Detection Time3. False Positive Rate: Indicates how many of the issues flagged during testing were not actual threats.
Why it matters: A low false positive rate helps your team focus on genuine issues without wasting time on irrelevant alerts.
False Positive Rate = (Number of False Positives ÷ Total Detected Issues) × 1004. Security Requirements Coverage: Assesses the percentage of defined security controls (like authentication, encryption, and access control) that are tested by your plan.
Why it matters: Ensures critical areas are not left untested and compliance needs are fully met.
Coverage = (Number of Security Requirements Tested ÷ Total Security Requirements) × 1005. Post-Deployment Incident Frequency: Tracks how often security issues arise after the application is deployed to production.
Why it matters: A low incident frequency means your pre-release security testing is effectively preventing real-world breaches.
Incident Frequency = Number of Security Incidents ÷ Time Period (e.g., per month or quarter)6. Compliance Pass Rate: Measures how well your system adheres to regulatory requirements such as GDPR, HIPAA, or PCI-DSS.
Why it matters: High compliance rates reflect both a strong security posture and readiness for audits.
Compliance Pass Rate = (Number of Passed Compliance Checks ÷ Total Compliance Checks) × 100Challenges in Security Testing and How to Overcome Them
Security testing is a crucial part of ensuring your software is resistant to cyberattacks and meets cybersecurity compliance. However, implementing an effective security testing strategy comes with its own set of difficulties.
These challenges can threaten both the integrity and effectiveness of your cybersecurity measures, especially when using complex tools for security testing or managing software security testing services.

Key Security Testing Challenges:
- Evolving Cybersecurity Threats
New and sophisticated cyberattacks emerge daily. This makes it challenging to maintain an up-to-date security testing service that defends against the latest vulnerabilities and threats. - False Negatives in Security Testing Tools
Some security testing tools might fail to detect certain vulnerabilities, resulting in cybersecurity risks being overlooked. This limits the effectiveness of your software security testing. - Complex Configuration of Tools for Security Testing
Many cybersecurity technologies and testing tools require deep expertise. Misconfiguration can lead to poor results, missed threats, and gaps in security testing coverage. - Limited Security Test Coverage Across Systems
Often, security testing is only performed at the application level, ignoring APIs, networks, and databases, leaving areas untested and vulnerable. - Risks from Third-Party Integrations
Modern software relies on third-party APIs, packages, and services. These can become attack vectors if not properly tested using dedicated cybersecurity solutions or vulnerability scanning.
Final Thoughts on Building a Strong Security Test Plan
A well-structured security testing plan is crucial for protecting software from growing cybersecurity threats. It should include both manual and automated security testing tools, clear testing goals, and align with industry cybersecurity compliance standards. Early detection of vulnerabilities and strong security measures help ensure software resilience.
To stay effective, the plan must evolve with changing threats. Regular updates, cross-team collaboration, and continuous testing throughout the development lifecycle are essential. With a proactive and strategic approach to software testing, organizations can build safer applications and ensure trust, reliability, and long-term protection against modern cyber risks.
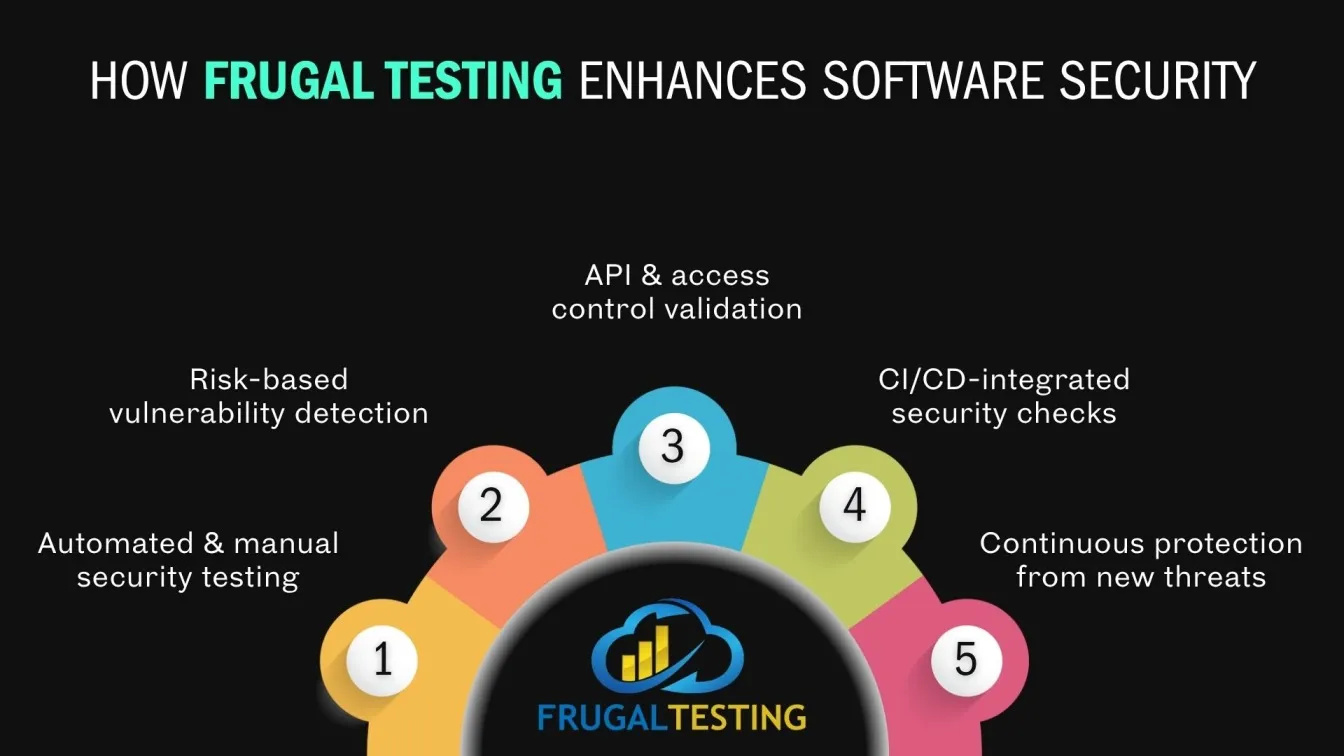
Frugal Testing is a leading SaaS application testing company known for its AI-driven test automation services. Among the services offered by Frugal Testing are cloud-based test automation services that help businesses improve testing efficiency, ensure software reliability, and achieve cost-effective, high-quality product delivery.
People Also Ask
👉 What is the NIST response plan?
The NIST response plan outlines how to prepare for, detect, respond to, and recover from cybersecurity incidents using a structured 4-phase approach.
👉 How to implement a successful cybersecurity plan?
Begin by assessing risks, defining security policies, setting objectives, and using tools and training to monitor and protect your systems continuously.
👉 How to create a security playbook?
A security playbook includes detailed response steps for specific threats, outlining team roles, tools, and timelines to ensure fast and coordinated action.
👉What is a SoA in cybersecurity?
SoA (Statement of Applicability) lists selected ISO 27001 controls and justifies their inclusion or exclusion, aligning with the organization's risk strategy.
👉 What are the phases of a cybersecurity incident response plan?
Key phases include Preparation, Detection, Containment, Eradication, Recovery, and Post-Incident Review to manage and recover from security breaches efficiently.



.webp)
%201.webp)

