As B2B enterprises seek to modernize their payment processing and optimize conversion rates, fintech apps like Apple Pay have surged ahead of traditional credit cards, offering streamlined checkout processes, enhanced security features, and richer customer experience. But with every new payment method comes fresh concerns about fraud, compliance, and technical integration. In this comprehensive guide, we’ll explore:

🔐 Key Insights
📌 What is Apple Pay & How it works at a technical level?
📌 The security architecture underpinning this mobile and online payment powerhouse
📌 Key technologies encryption protocols, tokenization, dynamic cryptograms that guard each transaction
📌A feature‑by‑feature comparison with Google Pay, Cash App, and other digital wallets
📌 Best practices for developers, QA teams, and software testing professionals to integrate Apple Pay seamlessly
Whether you’re evaluating payment processing options for your e‑commerce platform or a retail POS rollout, this deep dive equips you with the insights to decide if ApplePay and its companion Wallet app on Apple Watch and iPhone is the right fit for your organization.
What Is Apple Pay and How to Use It?
Apple Pay is Apple’s secure mobile wallet solution often stylized as apple pay that lets users make contactless payments in stores, within apps, and on the web without sharing their actual credit cards. Built into the Wallet app on iPhone, Apple Watch, iPad, and Mac, it leverages tokenization and biometric authentication for frictionless, PCI‑friendly transactions.
How to Set Up Apple Pay:
- Open the Wallet App: Tap the apple pay app icon on your device.
- Add a Card: Tap the “+” symbol and follow the prompts to scan or manually enter your credit card details from supported issuers (Visa, Mastercard, American Express).
- Verify with Your Bank: Complete one‑time verification via SMS, email, or your bank’s app.
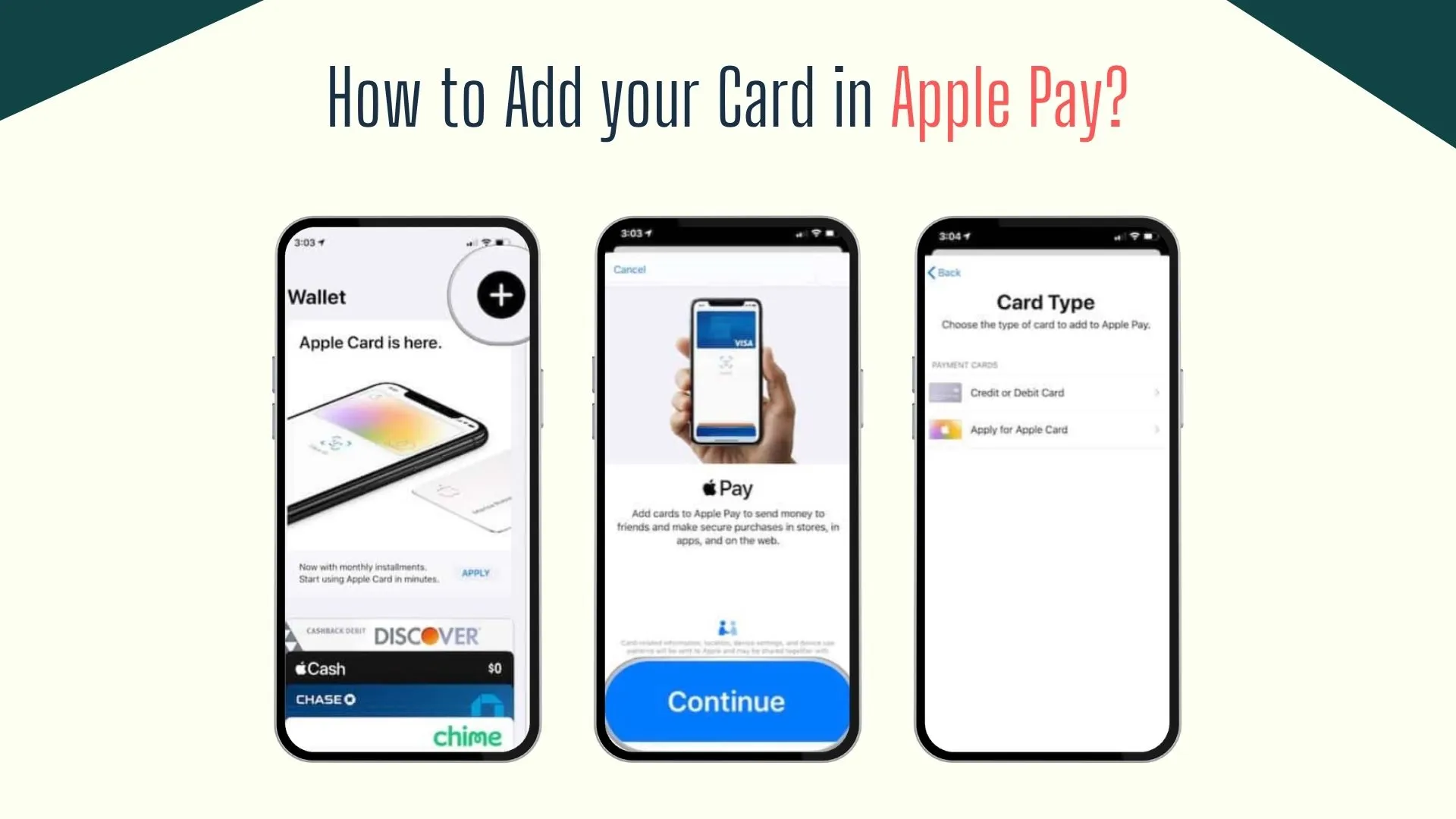
How to Use Apple Pay:
- In‑Store (NFC): Unlock your device with Face ID, Touch ID, or passcode, then hold it near the contactless reader until you see “Done.” No internet needed for the tap.
- In‑App & Online: At checkout, tap “Buy with Apple Pay,” confirm your payment method, and authenticate. Apple Pay auto‑fills shipping and billing details.
How Apple Pay Works: A Technical Overview for Businesses
Apple Pay leverages NFC‑based contactless taps and in‑app payment request APIs to replace physical credit cards with device‑specific tokens. Here’s the enterprise‑grade flow:
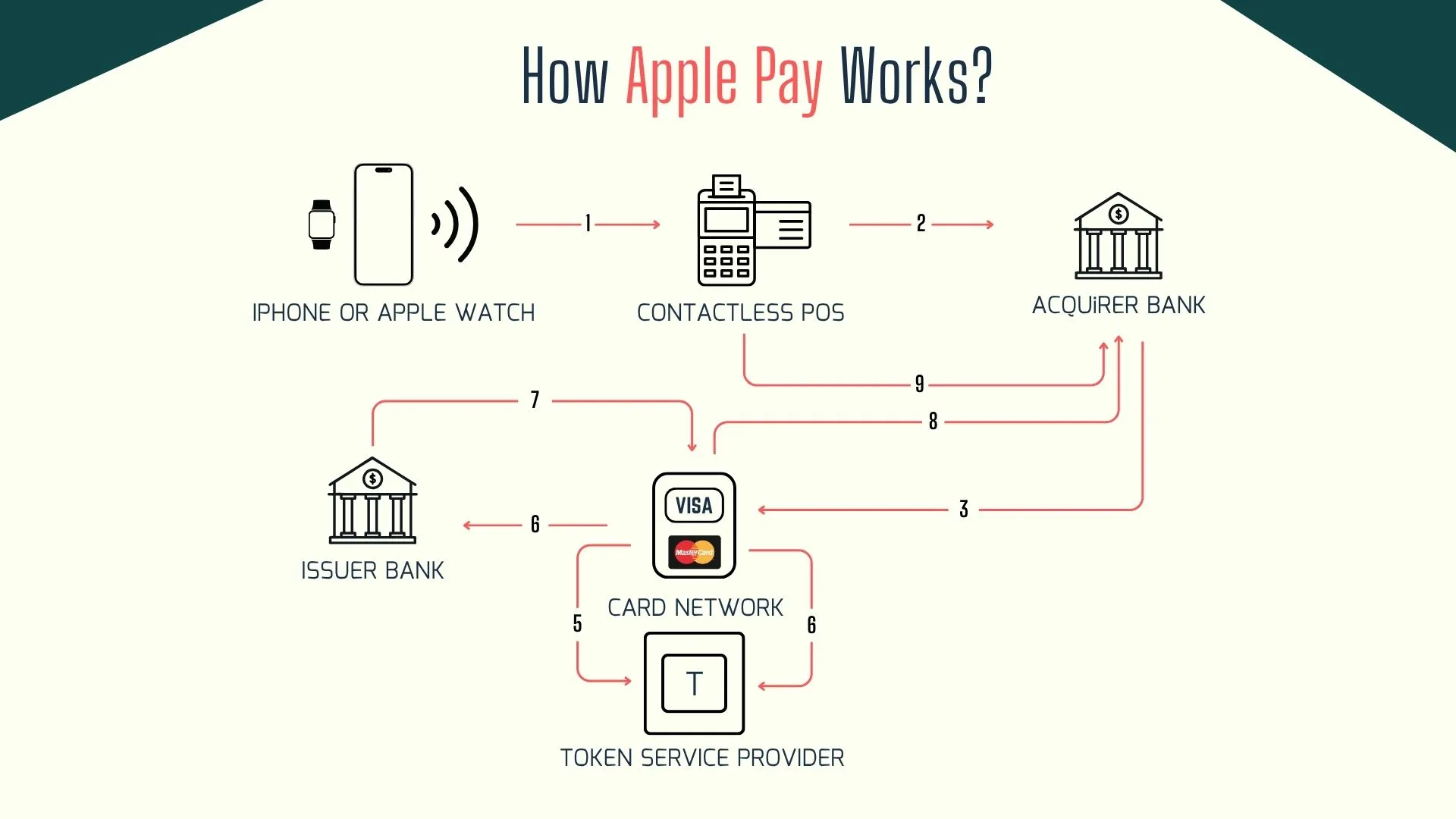
- Card Enrollment via Wallet App / Merchant ID Assignment
- Users add American Express, Visa, or Mastercard to their Wallet app on iPhone or Apple Watch.
- The payment processor (e.g., Adyen, Stripe) assigns a unique Merchant ID, and the issuing bank provisions a Device Account Number (DAN) into the Secure Element.
- Tokenization & Encryption Protocols
- Instead of the actual PAN, Apple Pay transmits the DAN plus a dynamic cryptogram. This process reduces PCI scope for merchants by keeping credit card data out of their systems.
- Instead of the actual PAN, Apple Pay transmits the DAN plus a dynamic cryptogram. This process reduces PCI scope for merchants by keeping credit card data out of their systems.
- Biometric & Passcode‑Enabled Consent
- Face ID or Touch ID-secured in the Secure Enclave-authorizes each transaction, ensuring only the authenticated user initiates payments.
- Face ID or Touch ID-secured in the Secure Enclave-authorizes each transaction, ensuring only the authenticated user initiates payments.
- Transaction Routing & Authorization
- The encrypted token travels through the payment network. The issuer decrypts it, validates the cryptogram and transaction details (amount, Merchant ID), then returns an approval or decline message.
- The encrypted token travels through the payment network. The issuer decrypts it, validates the cryptogram and transaction details (amount, Merchant ID), then returns an approval or decline message.
- Settlement & Real‑Time Payments
- Funds settle through familiar rails (Visa, Mastercard, ACH for bank‑linked wallets), supporting real‑time payments and international payments where networks allow.
This architecture ensures that merchants handle only encrypted tokens-streamlining compliance and defending against data breaches.
Is Apple Pay Secure? A Detailed Breakdown of Its Security Architecture
Apple Pay’s multi‑layered defense combines hardware, software, and network controls:
- Secure Element & Secure Enclave
A dedicated chip stores the DAN or Device Account Number and cryptographic keys, isolated from iOS. Biometric data and dynamic application security testing–backed processes run within the Secure Enclave, immune to malware and jailbreaking. - Tokenization & Dynamic Cryptograms
Each payment method-whether in-store NFC or online payments-uses a one-time cryptogram tied to the specific transaction amount, Merchant ID, and device. This thwarts replay attacks and skimming. - Biometric Authentication
Face ID / Touch ID integration demands physical presence, preventing remote fraud. For unattended terminals, a device passcode acts as a fallback.
- Fraud Detection & Analytics
Issuers and payment processors layer AI‑driven fraud detection on top of tokenized flows, leveraging artificial intelligence and machine learning to spot anomalies in real-time payments and payment experiences.
By fusing hardware‑level isolation with advanced encryption protocols, Apple Pay maintains an enterprise‑grade security posture that few digital wallets can match.
Key Technologies Behind Apple Pay’s Security Infrastructure
Apple Pay’s ironclad security relies on three core technologies - tokenization, the Secure Enclave with biometric authentication, and dynamic cryptograms that work together to shield card data, verify users, and ensure each transaction is uniquely protected.
Tokenization: Replacing Card Data with Secure Payment Tokens
Tokenization replaces your actual credit card number with a unique device‑specific DAN. When you add a card to Apple Pay, the Wallet app doesn’t store your actual Primary Account Number (PAN). Instead, Apple’s servers request a unique Device Account Number (DAN) from the card issuer, which is bound exclusively to your device.
This DAN is cryptographically secured and stored in the Secure Element - a purpose‑built chip isolated from iOS or watchOS so that every merchant transaction uses only this surrogate token.
If a breach occurs at the point of sale, attackers only obtain useless tokens, not real card data. Moreover, because DANs can be individually suspended or revoked through Apple Business Manager, organizations can quickly deprovision devices without having to reissue physical cards.
Secure Enclave and Biometric Authentication
The Secure Enclave is a dedicated co‑processor embedded in Apple devices that handles sensitive operations like key management and biometric matching. When you enroll Face ID or Touch ID, your facial map or fingerprint template is encrypted and stored solely within this hardware enclave - it never leaves the chip or becomes part of your broader iOS image.
At transaction time, the system performs a local challenge‑response: the Secure Enclave verifies your identity, unlocks the DAN’s private key, and signs the payment request. Because the enclave sits behind multiple hardware‑verified barriers (secure boot, memory encryption), even a compromised OS kernel cannot intercept or tamper with biometric data or cryptographic keys.
Dynamic Cryptograms and Device‑Specific Transactions
Each Apple Pay transaction is fortified by a one‑time cryptographic signature known as a dynamic cryptogram (akin to EMV’s Application Cryptogram). Generated using the DAN’s private key and a transaction‑specific nonce (an unpredictable number), the cryptogram proves both the device’s authenticity and the freshness of the request.
When the merchant forwards the payment to the issuer, the issuer’s backend validates the cryptogram against its copy of the DAN public key - if anything about the amount, merchant ID, or nonce doesn’t match, the transaction is instantly rejected. This per‑transaction signature ensures that even if an attacker could eavesdrop on an Apple Pay message, they could never replay or alter it to perform fraudulent charges.
How Apple Pay Prevents Fraud in High‑Risk Environments
In high‑risk, high‑volume settings like transit hubs and stadiums - Apple Pay combines skimming‑proof NFC, remote device lockdowns, and real‑time AI‑driven monitoring to stop fraud before it happens.
- Eliminate Skimming & Cloning
By using NFC instead of a magnetic stripe, Apple Pay transactions never expose your actual card data. Each payment generates a one‑time cryptographic token, so even if a thief tried to attach a skimmer to the terminal, there’s nothing of value to capture or clone. This makes traditional “copy‑and‑charge” attacks virtually impossible. - Lost Device Mitigation
If your iPhone or Apple Watch goes missing, you can immediately suspend Apple Pay through the Find My service. With a few taps in the Find My app or via iCloud.com, the device can be locked or wiped, instantly disabling any stored payment credentials and blocking unauthorized purchases. - Real‑Time Monitoring
Every tokenized transaction feeds into advanced fraud‑detection systems run by Apple’s payment partners. These platforms evaluate hundreds of signals—such as spending patterns, location changes, and device health—in real time. Unusual activity triggers instant risk scoring, allowing suspicious transactions to be flagged or halted before they clear.
This comprehensive approach slashes fraud rates, even under peak, mission‑critical loads.
Comparing Apple Pay with Other Mobile Wallets for Enterprise Payments
Before committing to a mobile wallet, enterprises must weigh trade‑offs in security, compliance, and integration complexity. The table below pits Apple Pay against Google Pay and Cash App across crucial criteria helping you pinpoint the optimal solution for your payment ecosystem.
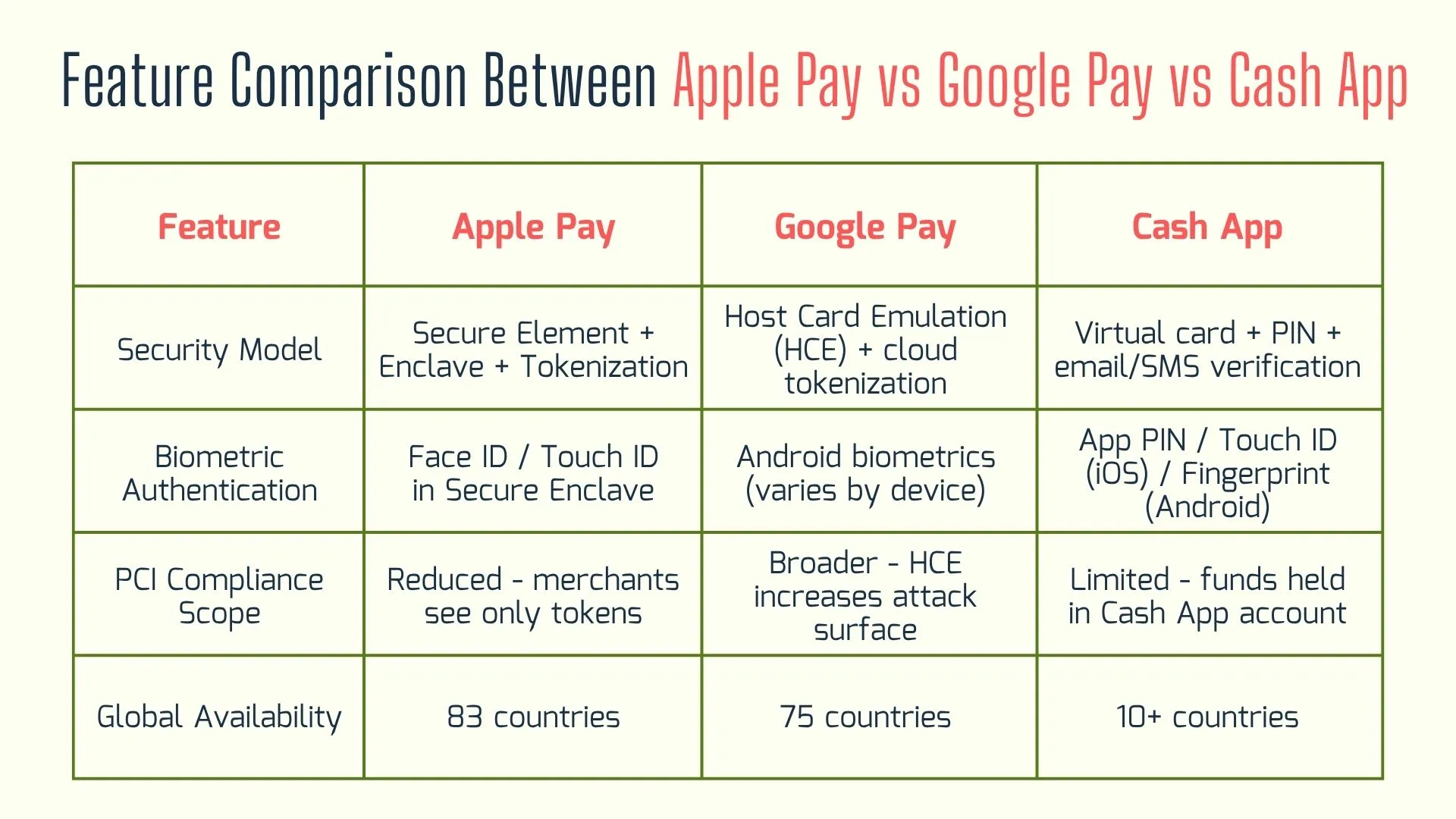
For organizations prioritizing tight security features, minimized software testing life cycle, and robust network security testing, Apple Pay remains the top choice.
Apple Pay Integration Best Practices for Developers and QA Teams
- Sandbox Testing & Test Mode
Leverage Apple Pay’s test mode in Xcode and the Wallet sandbox. Simulate payment methods for small business scenarios, error codes, and edge cases without real funds. - Automated End‑to‑End Testing
Use automation testing tools like selenium automation testing, XCTest, or Appium. Create scripts that simulate biometric approvals and validate both online payment methods and in‑store NFC flows. - Security Testing Services
Engage in security penetration testing, network security testing, and dynamic application security testing. Ensure that third‑party SDKs, including Cash App or Google payment methods, don’t introduce vulnerabilities. - Adhere to HIG & Checkout UX Guidelines
Follow Apple’s Human Interface Guidelines to maintain trust. Position the Apple Pay button prominently in the checkout process to boost conversion rates. - Continuous Monitoring & Analytics
Integrate your payment processor dashboard with real‑time alerts. Monitor metrics like transaction success rates, authorization declines, and chargebacks to optimize payment experiences. - Call‑to‑Action
Leverage expert software testing services to validate your Apple Pay integration. Schedule a demo or request a security testing consultation to ensure seamless deployment.
Conclusion: Why Apple Pay Is a Smart Choice for Security‑First Enterprises
Apple Pay stands out by combining hardware‑backed tokenization that dramatically reduces PCI scope, biometric authentication secured within an isolated Secure Enclave, and dynamic cryptograms paired with robust encryption protocols.
It also delivers solid support for real‑time payments, international payments, and Open Banking integrations, all while providing rich analytics through Apple Business Manager to drive higher conversion rates and an exceptional customer experience.
Whether you’re a global e‑commerce platform, brick‑and‑mortar retailer, or a software testing company building the next generation of payment processing solutions, Apple Pay offers enterprise‑grade security, scalability, and peace of mind.
Ready to accelerate your digital wallet strategy and safeguard your bottom line? Contact Frugal Testing for a free Apple Pay integration assessment, specialized automation testing services, and expert guidance on leveraging Apple Pay, Google Pay, and other payment methods.
FAQs
👉 Does Apple Pay work without internet?
Yes. In‑store NFC transactions occur entirely between the terminal and the Secure Element; no active internet connection is needed. However, to add cards or check your payment history, internet access is required.
👉 Is Apple Pay safer than a credit card?
Absolutely. Apple Pay never transmits your actual card number. Instead, it uses tokenization, dynamic cryptograms, and biometric locks, dramatically reducing skimming and cloning risks.
👉 What is the test mode for payment?
Test mode refers to Apple Pay’s sandbox environment in Xcode. Developers simulate payment methods, including google payment methods, amazon payment methods, and Costco payment methods, to validate flows without real transactions.
👉 What is PMT vs PMS?
- PMT (Payment Method Tokenization): Converting PAN into a unique token.
- PMS (Payment Management System): Back‑end infrastructure handling token provisioning, transaction routing, and reconciliation.
👉 How do I verify an ACH payment?
ACH verification uses micro‑deposits: two small deposits to the user’s bank account. Once the user confirms the amounts, it proves account ownership. While Apple Pay focuses on card and mobile wallet transactions, ACH remains the standard for direct bank transfers.





%201.webp)