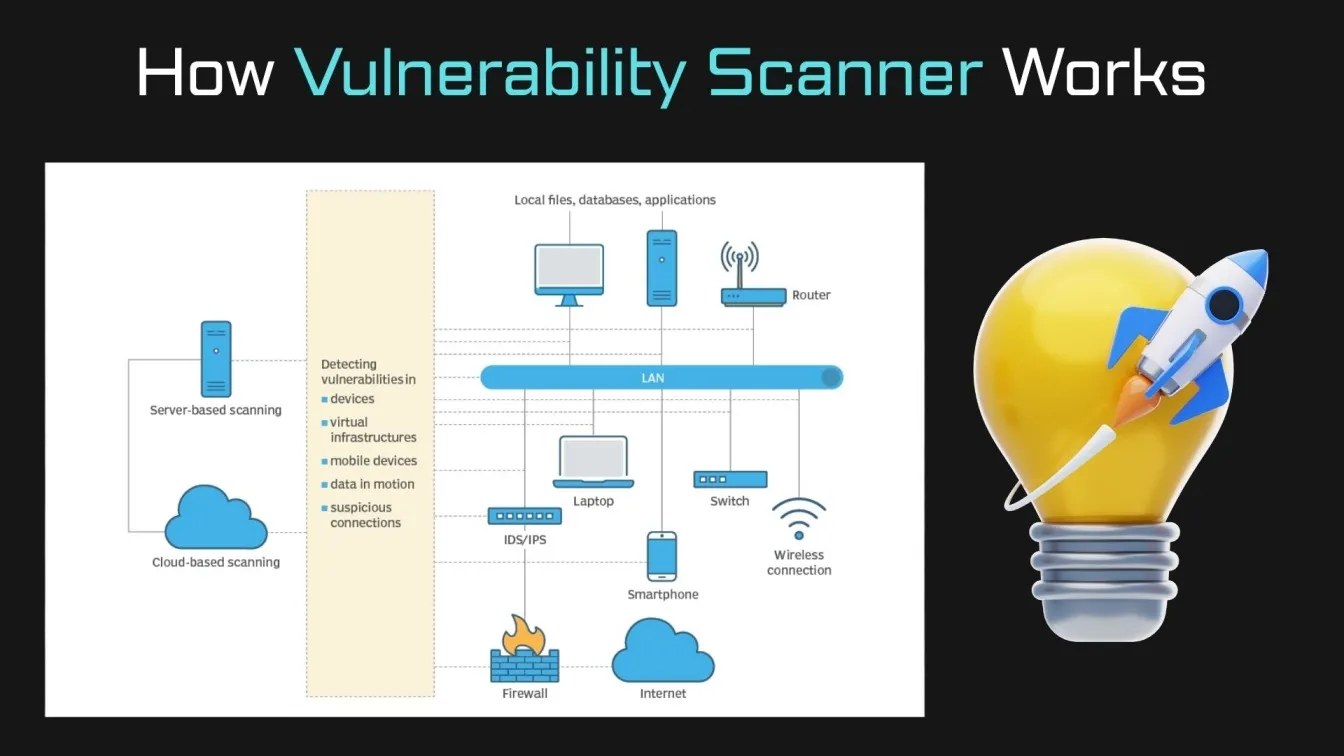
Securing a remote workforce is one of the most significant challenges businesses face in today’s digital age. As teams increasingly rely on cloud services, mobile devices, and connected devices, the risk of cyber attacks and security threats grows exponentially. Vulnerability scanning is a vital cybersecurity measure that helps identify and assess security vulnerabilities before they can be exploited by malicious actors. These scans are crucial for detecting weaknesses in systems, networks, and applications, such as unpatched software and weak security configurations. For remote teams, who often work across multiple devices and networks, regular vulnerability assessments are necessary to ensure business continuity and protect sensitive data from cybersecurity risks.
By utilizing vulnerability scanning tools and leveraging risk-based vulnerability management, organizations can address high-risk vulnerabilities, stay compliant with regulatory requirements, and ensure the integrity of their cloud infrastructure and cloud environment. This proactive approach enables businesses to identify vulnerabilities across both internal and external scans, secure their entire network, and safeguard their remote devices and mobile devices. Through effective remediation efforts and ongoing manual testing, businesses can reduce their risk profile and maintain a secure remote workforce. Vulnerability scanning is not just a preventative measure, it’s a strategy for staying ahead of the evolving threat landscape and protecting against critical threats.
What You Will Gain From This Blog?
📌 Understand the importance of vulnerability scanning in identifying critical vulnerabilities within your remote workforce.
📌 Learn how to distinguish between false positives and genuine vulnerabilities to streamline your remediation efforts.
📌 Discover best practices for cybersecurity professionals and how they can enhance their approach with regular vulnerability assessments and vulnerability examples.
📌 Explore the role of a dedicated security team in managing vulnerability scanning tools to stay compliant with regulatory requirements.
📌 Gain insights into risk-based vulnerability management and how it helps optimize your risk profile by focusing on high-risk vulnerabilities.
What Is Vulnerability Scanning and Why It’s Crucial for Remote Teams
Vulnerability scanning is the process of identifying and assessing potential weaknesses in a system that could be exploited by cybercriminals. It’s a critical part of cybersecurity, especially for remote teams, who often rely on a variety of devices and networks that can be more vulnerable to attacks. For remote workforces, vulnerability scanning is essential for protecting sensitive data, maintaining the integrity of systems, and ensuring that employees' devices and networks are secure from cyber threats.
With the rise of remote work, teams are spread across different locations, often using personal devices and networks that might not have the same security measures as company-managed infrastructure. Vulnerability scanning helps to identify security vulnerabilities in these systems before hackers can exploit them. This proactive approach to vulnerability management allows businesses to stay ahead of cyber risks and keep their operations secure.
Penetration Testing versus Vulnerability Scanning
It’s important to understand the difference between penetration testing vs vulnerability scanning. While both are crucial for maintaining security, they serve different purposes.
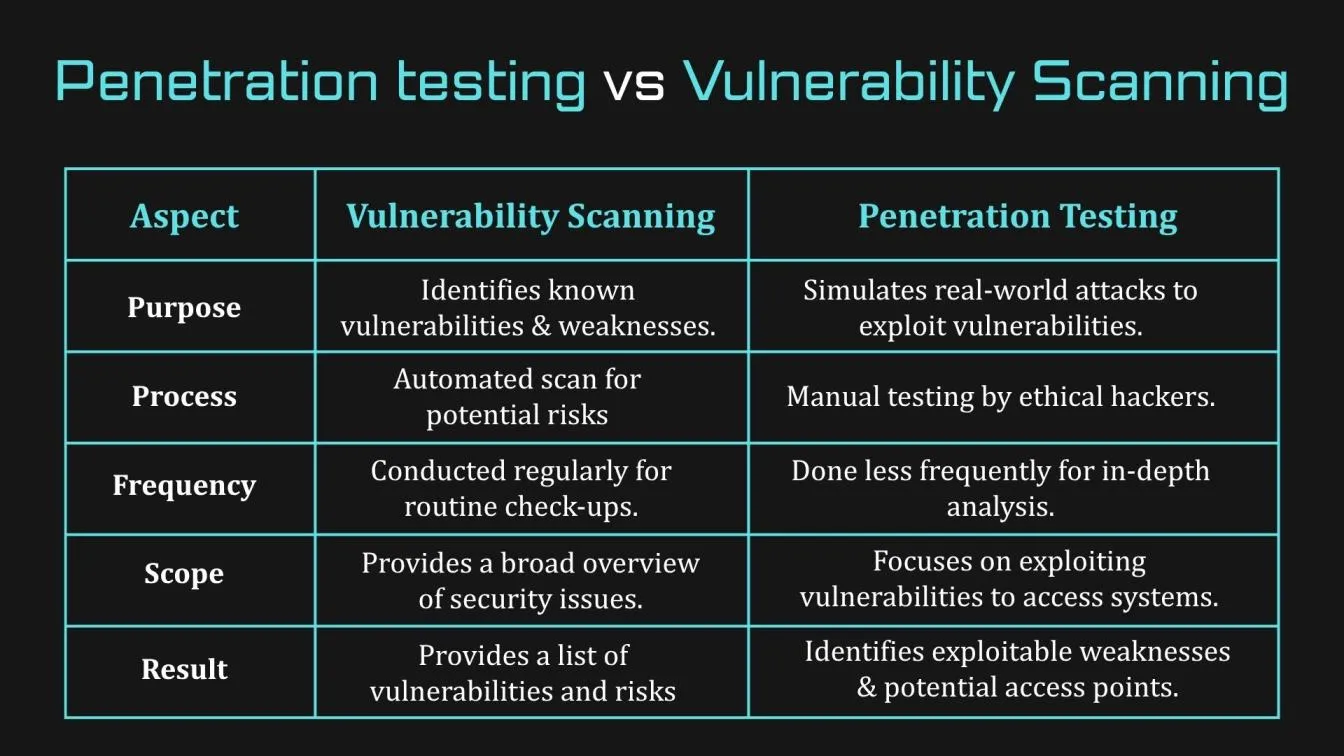
- Vulnerability scanning is an automated process that scans systems for known vulnerabilities and weaknesses. It provides a broad overview of potential risks but doesn't test if these vulnerabilities can actually be exploited.
- Penetration testing, on the other hand, is a more in-depth process where ethical hackers actively attempt to exploit vulnerabilities to see if they can gain unauthorized access. It’s a manual process that simulates real-world attacks.
Both are important, but vulnerability scanning is typically done more frequently as part of a regular security check-up, while penetration testing is used to dig deeper into the system's defenses.
Types of Vulnerability Scanning
There are several types of vulnerability scanning used to protect systems and data. Each type focuses on different aspects of your security infrastructure. Here are some of the most common types:
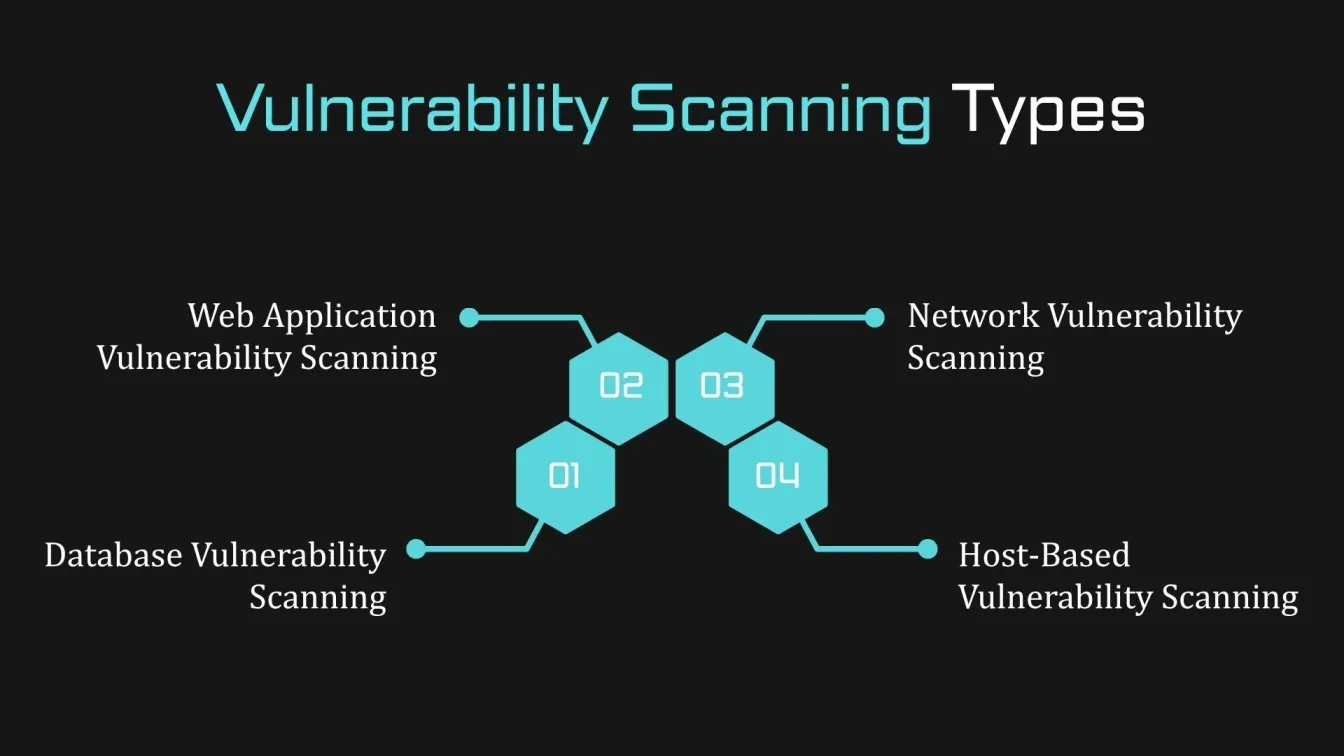
- Network Vulnerability Scanning: This type focuses on scanning the network for weaknesses, such as misconfigured firewalls, open ports, or outdated software. It helps identify issues that could allow unauthorized access to systems.
- Web Application Vulnerability Scanning: Since remote teams often rely on web applications for their work, scanning these apps for website vulnerabilities is crucial. This type of scan identifies vulnerabilities like SQL injection, cross-site scripting, and other common web application security flaws.
- Host-Based Vulnerability Scanning: Host-based scans focus on individual devices, such as laptops, desktops, and servers, looking for outdated software or vulnerabilities in operating systems that could lead to data breaches.
- Database Vulnerability Scanning: This scan looks for issues in databases, like improper configuration or weak authentication methods that could expose sensitive data.
Each of these types of scans plays a role in building a secure remote workforce by identifying and managing cybersecurity risks before they lead to a security breach.
What Is a Remote Workforce and Why It Matters
A remote workforce refers to employees who work from locations outside of a traditional office setting, often relying on cloud-based tools and digital communication to perform their job. Remote teams can be located anywhere globally, making it easier for businesses to tap into a broader talent pool.

However, managing a remote workforce brings its own challenges. Security is a primary concern, as employees often use personal devices and unsecured networks that can increase the risk of cyberattacks. Vulnerability scans are essential in this context to identify potential threats before they can cause damage. Ensuring that remote workers follow security protocols and have the necessary vulnerability testing tools to stay protected is crucial for maintaining the overall security of the organization.
Challenges Faced by Remote Workforces and How to Overcome Them
While remote work offers many benefits, it also poses several challenges, particularly when it comes to cyber risks. Some of the most common challenges include:

- Insecure Networks: Many remote workers connect to public or personal Wi-Fi networks, which may not have the proper security protections. This increases the likelihood of hackers intercepting sensitive data.
- Device Security: Employees often use personal devices for work, which may not be as secure as company-issued hardware. Without proper vulnerability assessment on these devices, they can become easy targets for cybercriminals.
- Lack of Cybersecurity Awareness: Remote workers may not be aware of the best practices to secure their devices, such as using strong passwords, enabling two-factor authentication, or regularly updating their software.
The solution to these challenges lies in vulnerability management. Regular vulnerability scans can help identify issues, while employee training on security best practices can reduce the risk of human error. By using vulnerability scanning tools and implementing secure remote work solutions, businesses can mitigate these risks and ensure a safer work environment.
How Vulnerability Scanning Works to Identify Threats
Vulnerability scanning works by automatically identifying potential security weaknesses in systems, networks, or applications. The scanning process involves the following steps:
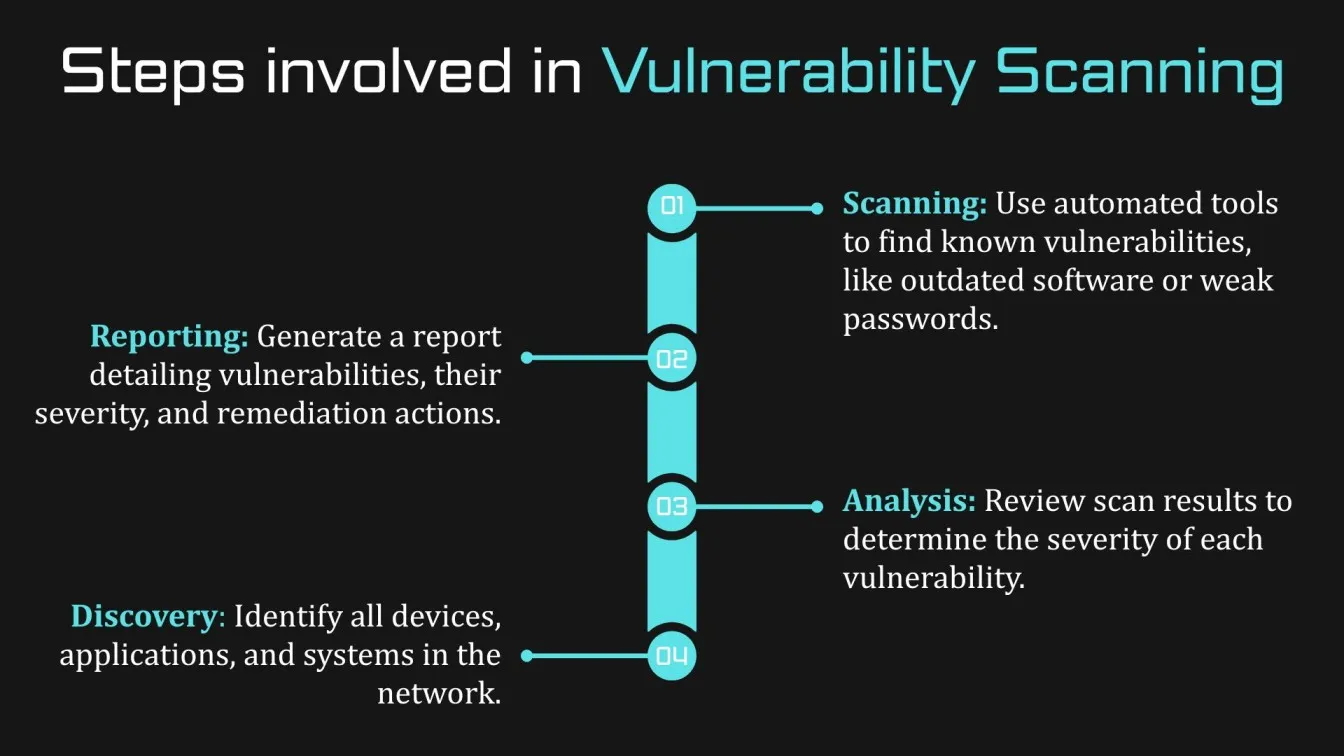
- Discovery: The first step is to identify all devices, applications, and systems in the network. This ensures that every asset is monitored for vulnerabilities.
- Scanning: Using automated tools, the scan looks for known vulnerabilities, such as outdated software, weak passwords, or unpatched systems.
- Analysis: Once the scan is complete, the results are analyzed to identify the severity of each vulnerability. This allows businesses to prioritize which vulnerabilities need to be fixed first.
- Reporting: After the scan, businesses receive a vulnerability report detailing the issues found, their severity, and recommended actions for remediation.
By running regular vulnerability scans, businesses can identify and address security vulnerabilities before they are exploited, ensuring that their remote workforce remains protected from cyber threats.
Top Benefits of Vulnerability Scanning for Remote Workforce Security
Vulnerability scanning provides multiple benefits for ensuring the security of a remote workforce. These benefits go beyond just identifying weaknesses; they help create a proactive approach to cybersecurity. Here are the top benefits:
- Early Detection of Security Risks: Regular vulnerability scanning helps in identifying security vulnerabilities before hackers can exploit them. By addressing issues early, companies can prevent major security breaches.
- Reduced Attack Surface: By scanning systems and networks for vulnerabilities such as outdated software or weak passwords, businesses can reduce the points of entry for cybercriminals.
- Compliance with Regulations: Many industries have strict regulations regarding vulnerability management and cybersecurity risks. Regular scans help ensure compliance with these regulations and avoid potential penalties.
- Increased Trust and Confidence: When employees, customers, and partners know that a business is taking steps to secure its remote workforce, it builds trust. Proactive vulnerability management helps ensure the safety of sensitive data.
- Cost-Effective Security: Identifying and fixing vulnerabilities early is much more cost-effective than dealing with the aftermath of a data breach. Regular vulnerability assessments save businesses from costly downtime and reputation damage.
By integrating vulnerability scanning services into their security practices, companies can ensure a secure remote workforce, protecting both their employees and data from emerging threats.
Best Vulnerability Scanning Tools for Remote Workforce Protection
Choosing the right vulnerability scanning tool is crucial for securing your remote workforce. Here are some of the best tools that can help protect remote teams:
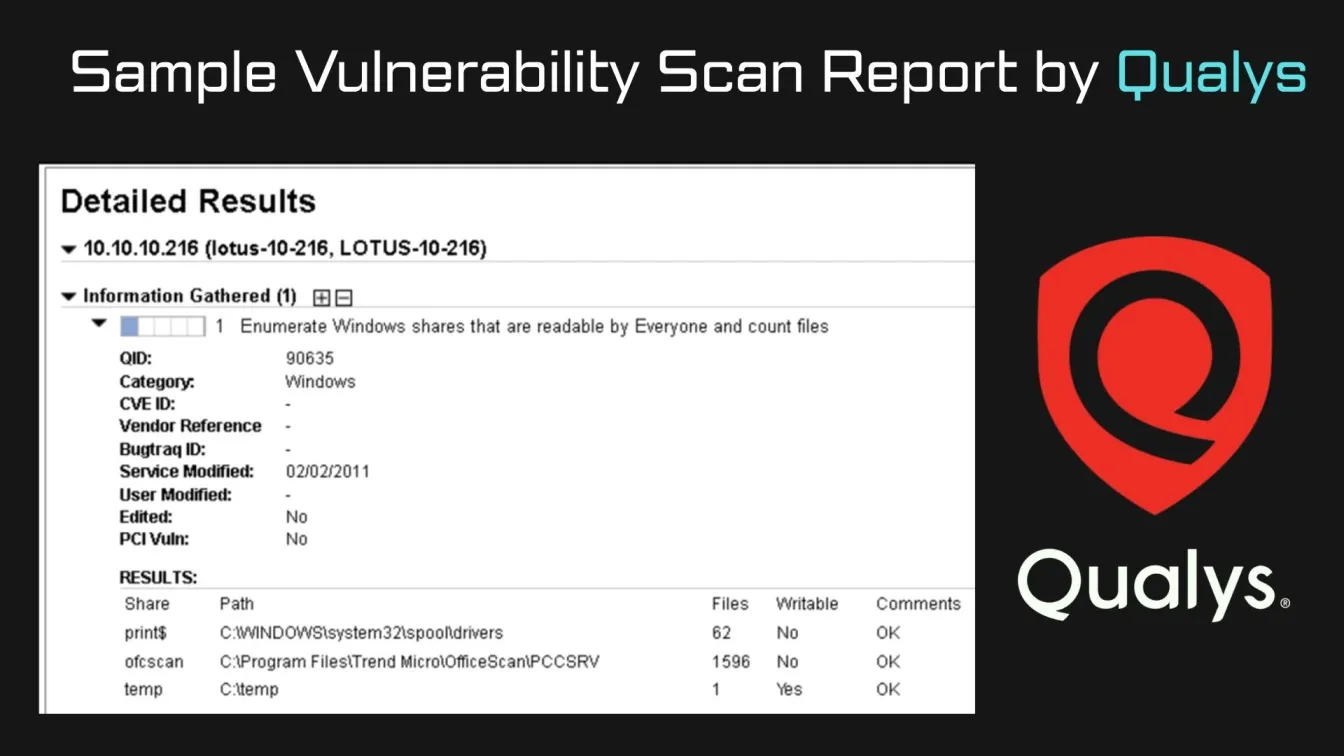
- Qualys: Qualys is a cloud-based platform that offers comprehensive vulnerability management solutions. It helps in scanning for vulnerabilities across networks, web applications, and databases, providing businesses with an all-encompassing security solution.
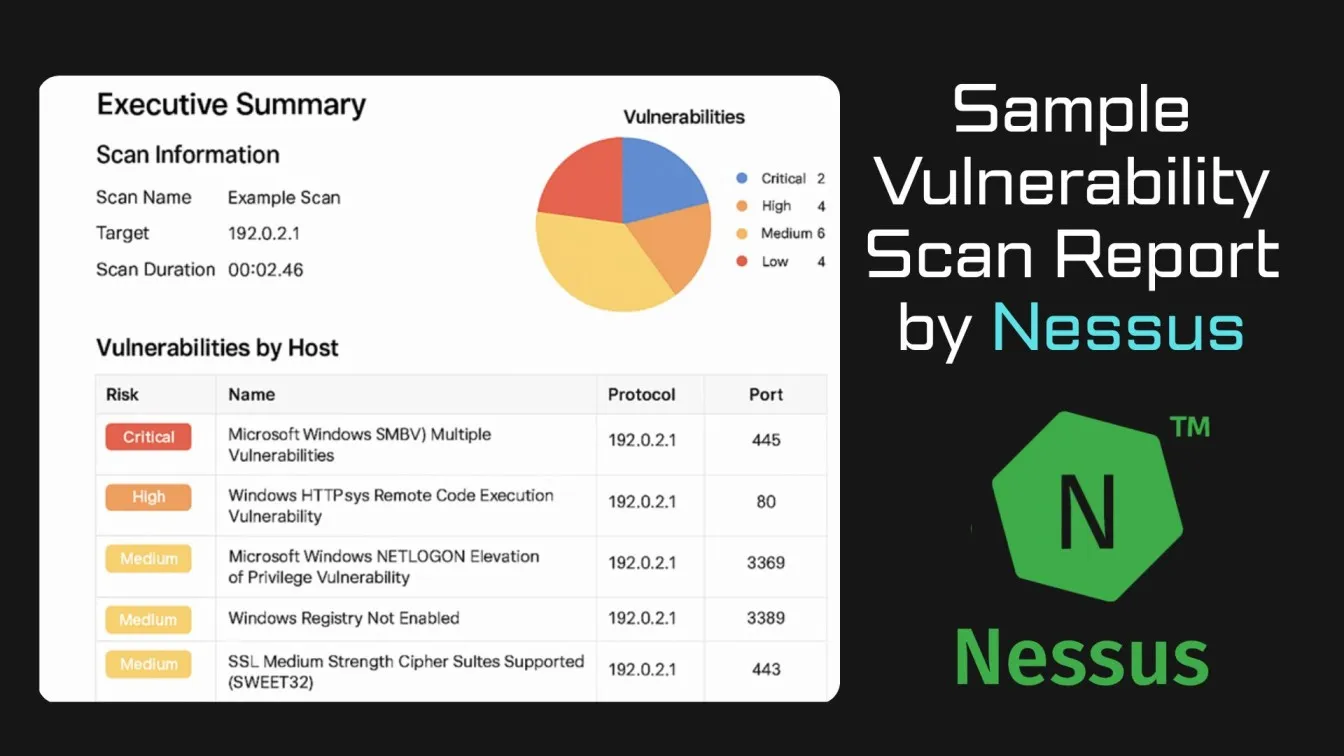
- Nessus: Nessus, a product of Tenable, is one of the most popular vulnerability scanning tools. It offers security vulnerability detection for a wide range of systems and applications, including website vulnerability scans. Nessus is known for its robust reporting capabilities and detailed vulnerability assessment.
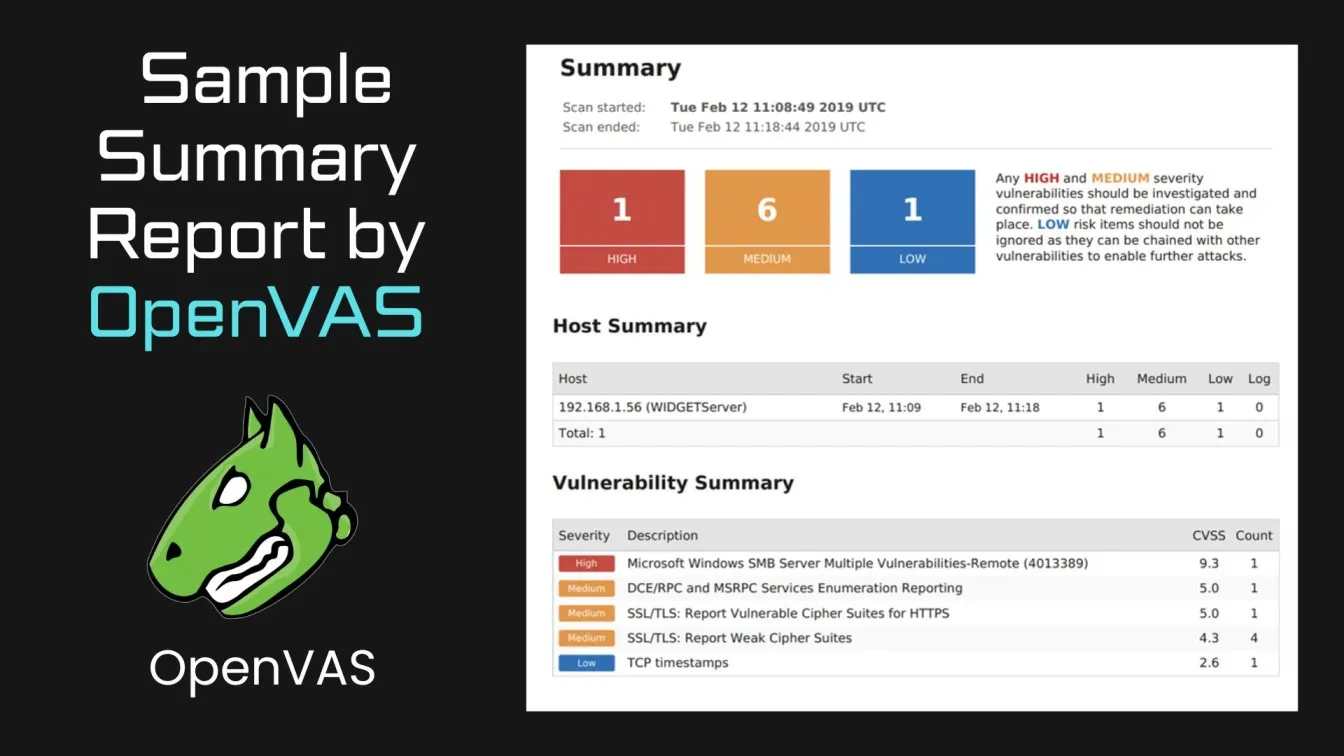
- OpenVAS: OpenVAS is an open-source vulnerability scanner that provides high-quality scans for identifying security flaws. It is ideal for businesses looking for a cost-effective solution to protect their remote workforce.
- Tenable.io: This cloud-based tool provides vulnerability management and continuous monitoring. It allows businesses to track vulnerabilities over time and offers integration with other security tools to enhance overall security.
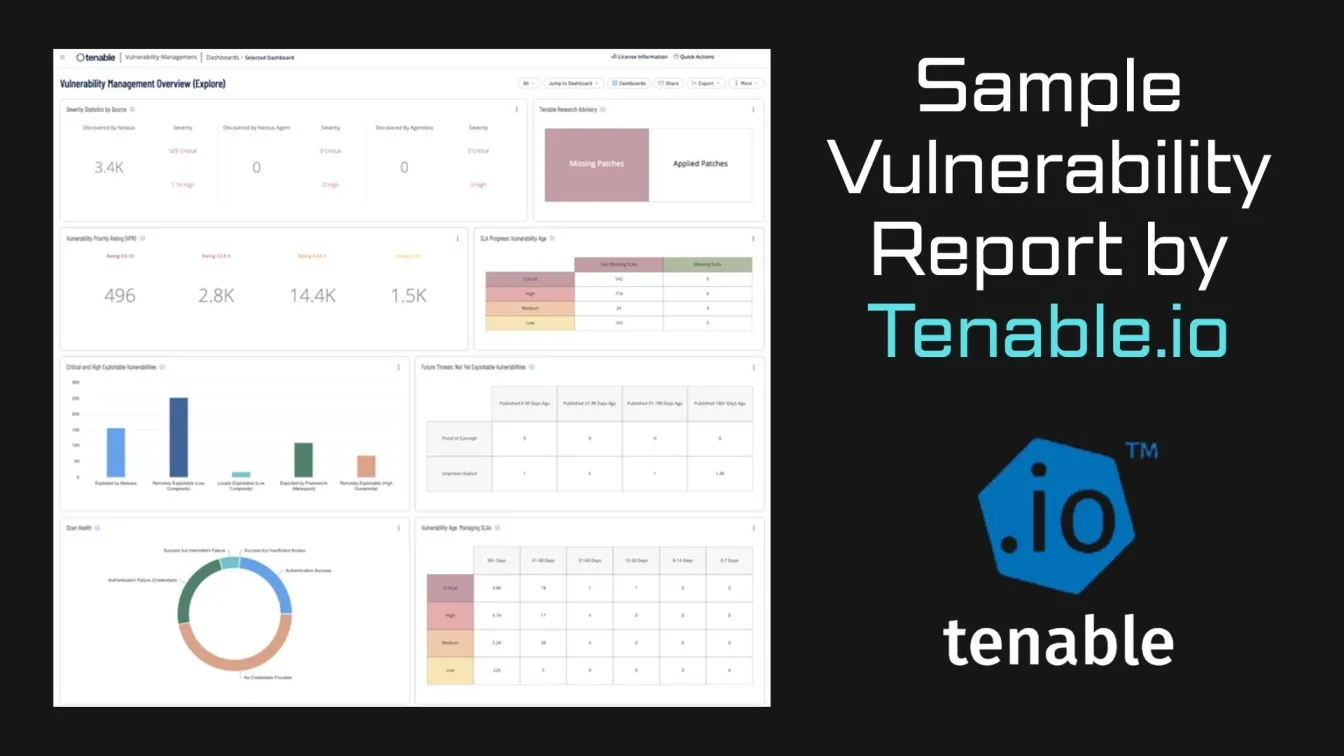
- Acunetix: Acunetix specializes in web application security, providing website vulnerability scanning to detect common vulnerabilities like cross-site scripting (XSS) and SQL injection. It's particularly valuable for businesses that rely heavily on web applications.
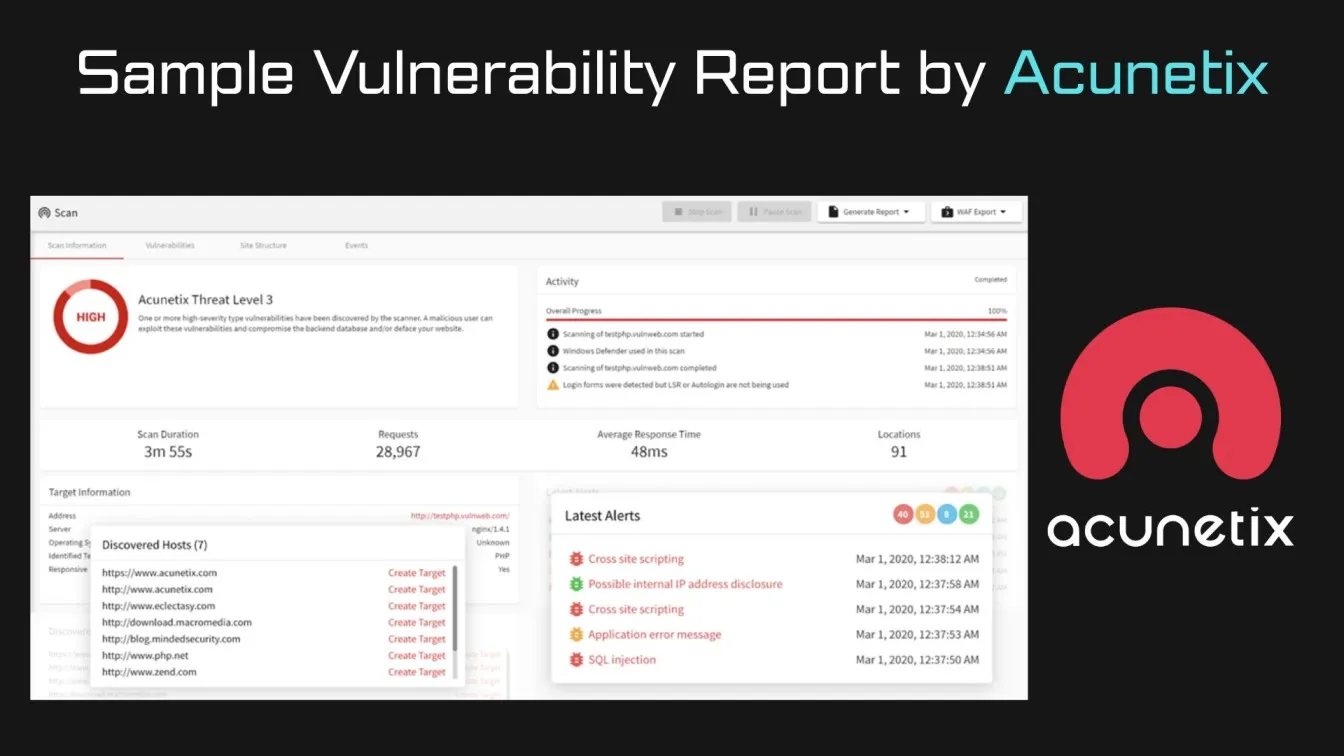
These tools offer a range of features to help businesses protect their remote workforce from cybersecurity risks. Implementing the right tool based on your business’s needs can significantly reduce the risk of vulnerability exploitation.
The Future of Remote Work Security: Emerging Trends in Vulnerability Scanning
As remote work continues to grow, the landscape of cybersecurity risks evolves. The future of remote workforce security will be shaped by emerging trends in vulnerability scanning. Here are some trends to watch out for:
- AI and Machine Learning Integration: AI-powered vulnerability scanning tools will enhance the ability to detect vulnerabilities faster and more accurately. Machine learning algorithms can analyze past incidents to predict potential security flaws and proactively address them.
- Cloud Security and Vulnerability Scanning: As more businesses migrate to the cloud, cloud-based vulnerability scanning will become even more important. With remote workforce software and cloud applications in use, it’s essential to have robust security measures in place to protect these environments.
- Real-Time Vulnerability Scanning: The future will see more businesses adopting real-time vulnerability detection, ensuring that any new vulnerabilities are identified and addressed immediately, reducing the window of exposure for remote workers.
- Automation in Vulnerability Management: Automated vulnerability management tools will become more common, helping businesses streamline their security practices. Automation can reduce human error and ensure that regular vulnerability scans are conducted without delay.
- Zero Trust Security: As part of an evolving security strategy, businesses will implement zero-trust models. This approach continuously verifies users and devices, reducing the risk of unauthorized access, especially within a remote workforce environment.
By staying ahead of these trends, businesses can better prepare for the future of remote work security, ensuring their remote workforce remains protected from emerging cybersecurity risks.
Training Your Remote Team: Best Practices for Vulnerability Scanning Awareness
While vulnerability scanning is essential for maintaining security, it’s also important to ensure that your remote workforce is aware of the threats and understands how to mitigate them. Here are some best practices for training your remote team on vulnerability scanning:
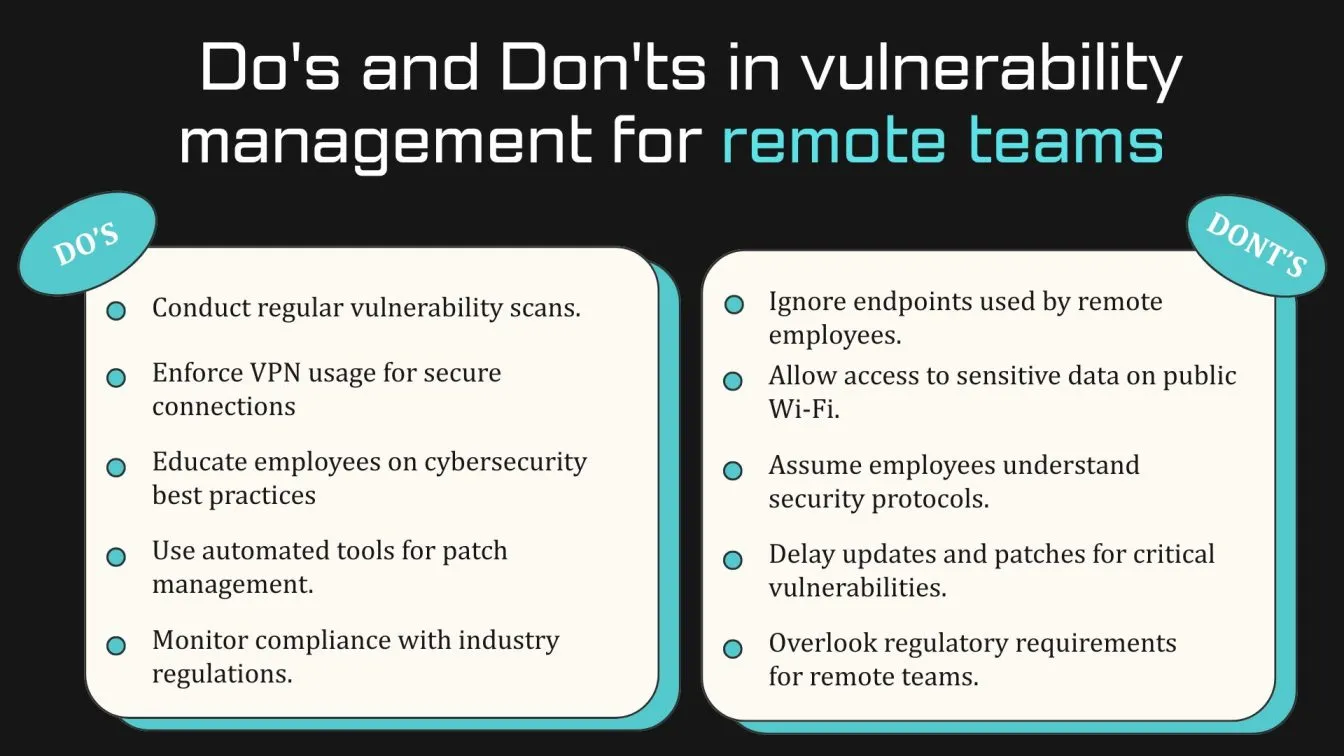
- Regular Training Sessions: Hold regular training sessions to educate employees about the importance of vulnerability management. Ensure that remote workers understand how vulnerabilities can impact the business and what steps they can take to prevent them.
- Promote Strong Password Practices: Encourage employees to use strong, unique passwords for all systems. Teach them about password managers and the importance of vulnerability detection for password-related vulnerabilities.
- Simulate Real-World Attacks: Use simulated phishing or other attack methods to help your team recognize potential threats. This hands-on approach can increase awareness and prepare employees to spot attacks before they cause damage.
- Encourage Regular Software Updates: Make sure your team understands the importance of keeping software up-to-date. Vulnerabilities often arise from outdated software, so regular updates are a crucial part of vulnerability management.
- Use Vulnerability Scanning Tools for Awareness: Provide employees with access to vulnerability scanning tools so they can perform scans on their personal devices. This hands-on experience can increase awareness of potential vulnerabilities in their systems.
Training your remote team on vulnerability scanning and security awareness is an ongoing process. By equipping your workforce with the right knowledge and tools, you can build a more secure remote workforce that is prepared to face cybersecurity risks head-on.
Wrapping it up
Ensuring the security of your remote workforce requires continuous vigilance and effective vulnerability scanning to stay ahead of emerging threats. By leveraging both internal scans and external vulnerability scans, businesses can identify and address critical issues within their legacy systems and critical assets. Scanning helps uncover blind spots that could be exploited by cybercriminals, especially in remote work environments where remote access is commonplace. Regular updates, including security patches, are key to safeguarding digital assets and maintaining the integrity of business operations.
Software Vulnerability management should be a key component of any DevOps team’s workflow, with a robust feedback loop ensuring that identified threats are promptly addressed. By maintaining updated vulnerability databases and generating detailed reports from scan reports, businesses can proactively manage security challenges and reduce the risk of lateral movement within their network, ultimately strengthening their security posture and protecting valuable data.
At Frugal Testing, we offer AI-driven test automation services to enhance the security and performance of your applications. As a leading software testing service provider, we deliver comprehensive functional testing solutions to ensure robust security and flawless functionality for your systems.
People also Asked
What is the difference between vulnerability scanning and security scanning?
Vulnerability scanning identifies specific weaknesses in systems, while security scanning examines overall security measures, including firewalls and intrusion detection.
Is Wireshark a vulnerability scanner?
No, Wireshark is not a vulnerability scanner; it is a network protocol analyzer. It captures and inspects network traffic to help troubleshoot issues, but it does not scan for security vulnerabilities like dedicated vulnerability scanners.
What is the difference between vulnerability scanning and security scanning?
Vulnerability scanning identifies system weaknesses, such as unpatched software or misconfigurations, while security scanning includes vulnerability scanning and evaluates overall security measures like firewalls and intrusion detection systems.
Is a SIEM a vulnerability scanner?
A SIEM (Security Information and Event Management) is not a vulnerability scanner. While it analyzes security data to detect threats, a vulnerability scanner identifies weaknesses in systems, networks, or applications that could be exploited.
Is Microsoft Defender a vulnerability scanner?
Microsoft Defender is not a vulnerability scanner; it focuses on antivirus and threat protection. It offers some vulnerability protection but lacks the depth of dedicated scanners.




%201.webp)