If you're into development, cybersecurity, or just love tech, understanding Vulnerability Assessment and Penetration Testing (VAPT) is crucial. This blog offers a clear and concise exploration of why VAPT is the smartest investment you can make for your product's security and success.
📌 Why read this blog?
- Gain insights into VAPT without technical jargon.
- Understand the benefits VAPT offers for your product's security and growth.
📌 What you'll discover:
- Introduction to VAPT: Why it's essential in today's cybersecurity landscape.
- Detailed Analysis: How Vulnerability Assessment and Penetration Testing identify and address security gaps.
- Evaluation of VAPT's Impact: How VAPT improves security, ensures data protection, and meets industry standards.
Introduction to Vulnerability Assessment and Penetration Testing (VAPT)
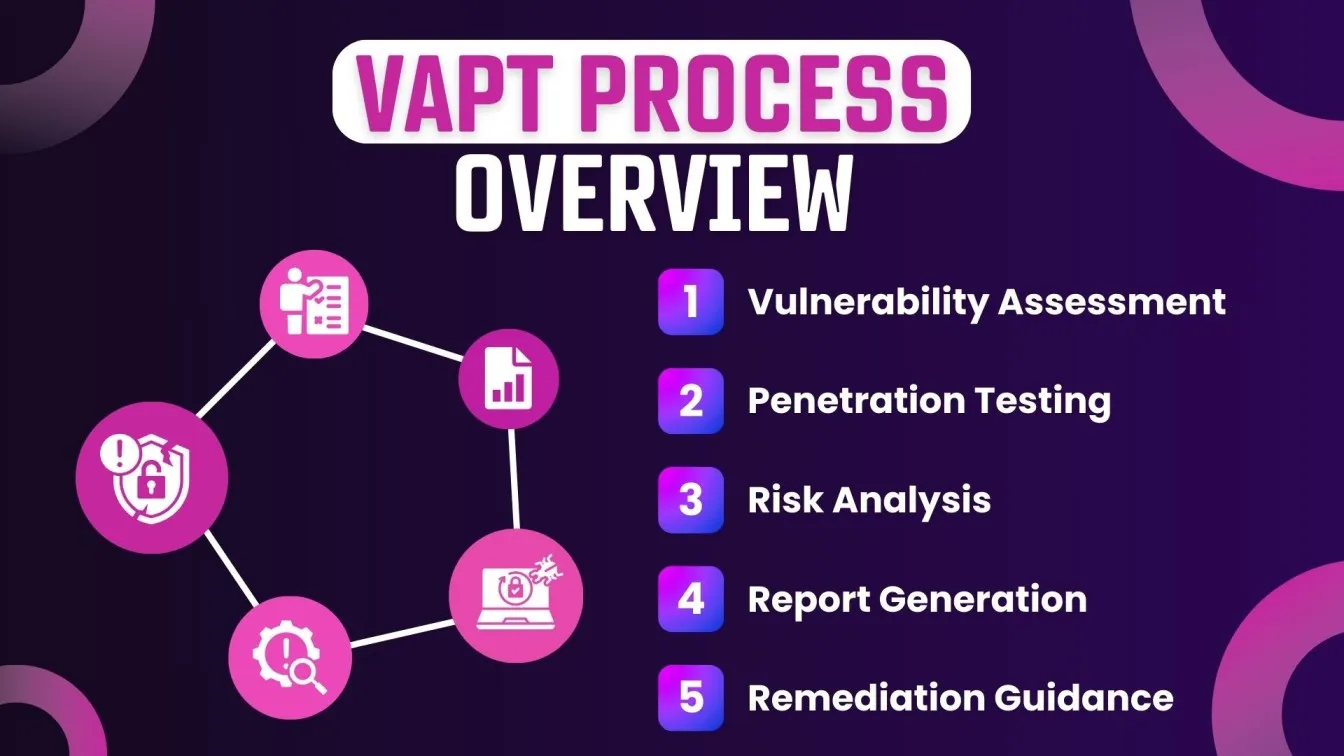
Vulnerability Assessment and Penetration Testing (VAPT) is a comprehensive security practice that involves two critical processes aimed at identifying, evaluating, and mitigating potential security vulnerabilities in a product, application, network, or system.
📌 Vulnerability Assessment:
- Purpose: The goal is to systematically identify, analyze, and prioritize security weaknesses in a system. This process uses automated tools and techniques to scan for known potential vulnerabilities.
- Process: This involves examining software and hardware systems to uncover potential security flaws, cyber threats, misconfigurations, and weaknesses that could be exploited by malicious actors.
- Output: Generates a report listing all potential vulnerabilities, categorized by severity, along with recommendations for remediation.
📌 Penetration Testing:
- Purpose: This is an active security exercise that simulates cyberattacks on a system to test the effectiveness of existing security measures.
- Process: Security professionals (often ethical hackers) attempt to exploit identified vulnerabilities to determine the potential impact of a real-world attack.
- Output: Provides a detailed report of the exploitability of the vulnerabilities and suggests measures to strengthen the security posture.
Why is VAPT Important for Product Security? 🤔
VAPT helps in identifying both known and unknown security vulnerabilities, allowing organizations to proactively address potential threats before they can be exploited by cybercriminals.
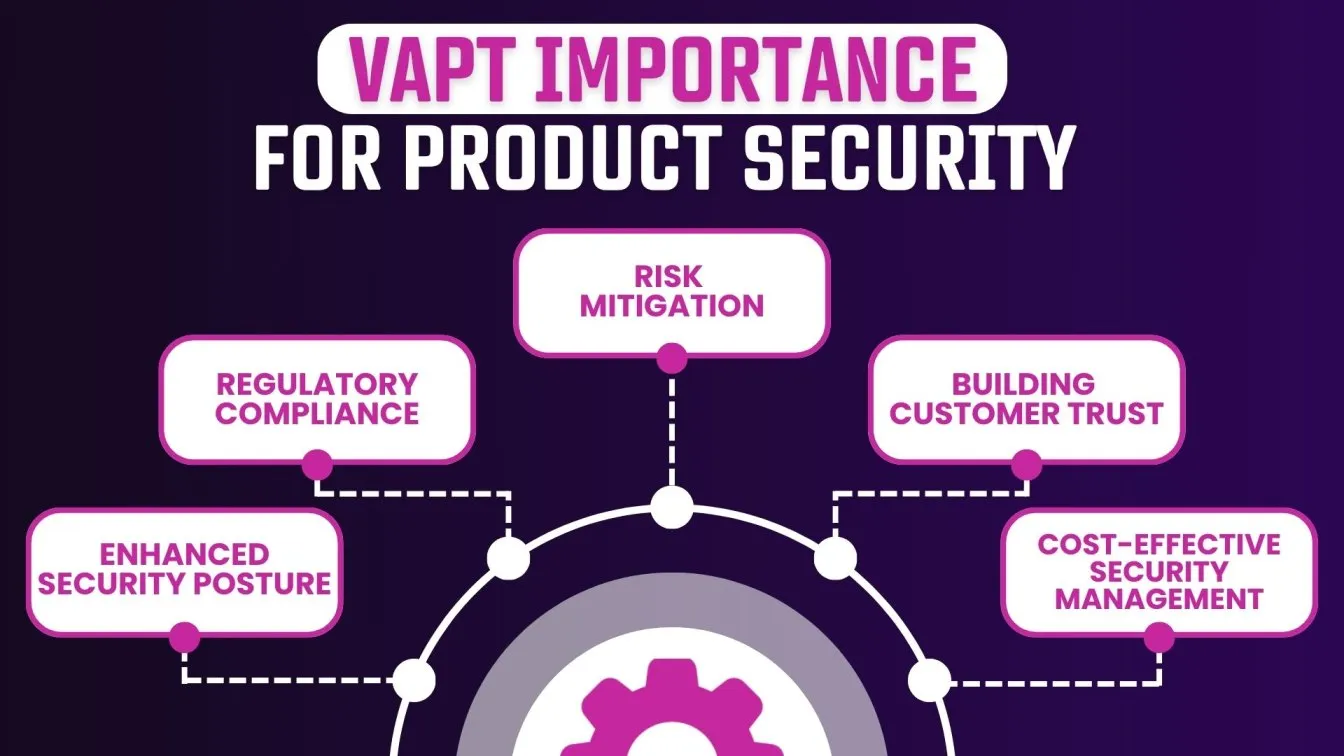
- Enhanced Security Posture:
- By discovering and addressing vulnerabilities, VAPT enhances the overall security posture of a product, ensuring that sensitive data is protected against unauthorized access and cyber threats.
- Regulatory Compliance:
- Many industries require compliance with security standards and regulations such as GDPR, HIPAA, PCI DSS, and ISO 27001. VAPT assists organizations in meeting these requirements by demonstrating due diligence in maintaining secure systems.
- Risk Mitigation:
- VAPT provides a clear understanding of the security risks associated with a product, allowing organizations to prioritize remediation efforts based on the severity of vulnerabilities. This proactive approach significantly reduces the risk of data breaches and cyber-attacks. 🔄
- Building Customer Trust:
- By implementing VAPT, organizations demonstrate a commitment to security and data protection. This builds trust with customers and stakeholders, enhancing the organization's reputation and credibility in the market.
- Cost-Effective Security Management:
- Identifying and fixing vulnerabilities early in the development lifecycle is more cost-effective than addressing security incidents post-breach. VAPT helps organizations save money by preventing costly data breaches and mitigating potential damage.
Scope of the VAPT
The scope of Vulnerability Assessment and Penetration Testing (VAPT) outlines the activities, systems, networks, applications, and data to be assessed for security vulnerabilities. Defining the scope is essential for ensuring that VAPT aligns with the organization's network security objectives and is both effective and comprehensive.
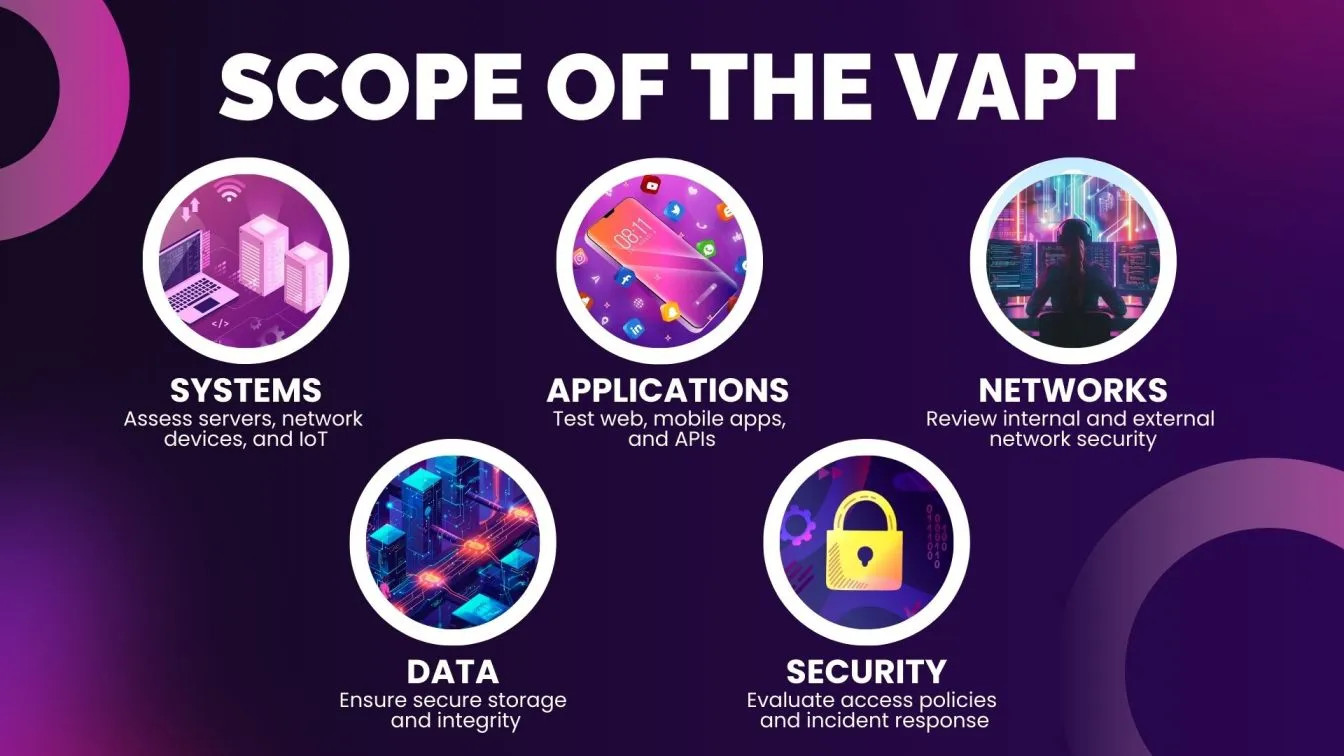
- System Components
- Servers: Evaluate physical and virtual servers, including web, application, and database servers.
- Network Infrastructure: Examine routers, switches, firewalls, and other networking equipment.
- IoT Devices: Regularly assess vulnerabilities in connected IoT devices.
- Applications
- Web Applications: Test for common vulnerabilities like SQL injection and cross-site scripting (XSS).
- Mobile Applications: Analyze security weaknesses in Android and iOS applications.
- APIs: Test APIs to ensure secure communication and data exchange.
- Networks
- Internal Networks: Assess the security posture, including segmentation and access controls.
- External Networks: Test perimeter defenses, including internet-facing services.
- Data and Information
- Data Storage: Examine data storage systems for unauthorized access and security holes.
- Data Integrity: Verify mechanisms to prevent unauthorized modification or tampering.
- Security Controls and Procedures
- Access Controls: Evaluate policies and mechanisms to ensure only authorized access to sensitive resources.
- Incident Response: Review incident response plans to assess readiness for security incidents.
How does VAPT differ from other cybersecurity measures?

Vulnerability Assessment and Penetration Testing (VAPT) differ from other cybersecurity measures in the following ways:
Benefits of outsourcing VAPT rather than conducting it in-house

Outsourcing Vulnerability Assessment and Penetration Testing (VAPT) can offer several benefits over conducting it in-house. Here are some key advantages:
1. Expertise and Experience:
🕵️♂️ Access to Specialists: External VAPT providers have specialized teams with extensive experience and up-to-date knowledge of the latest security threats, vulnerabilities, and testing methodologies. They often employ a mix of automated tools and manual pen tests to ensure comprehensive coverage.
🕵️♂️ Diverse Skill Sets: Outsourcing firms often have experts in various domains, offering a comprehensive approach to security testing that may not be available in-house. This can include testing for weak spots, such as vulnerabilities in operating systems, or assessing social engineering risks.
2. Return on Investment
🚀 Reduced Overhead: Outsourcing eliminates the need to hire, train, and maintain an internal security team, saving costs associated with salaries, benefits, and training. It also reduces the need for investment in vulnerability assessment tools, which can be expensive.
🚀 Scalability: You can scale services up or down based on project requirements without investing in additional resources or infrastructure, making it a strategic investment for your organization's security needs.
3. Objectivity
🛡️ Unbiased Perspective: External testers provide an impartial view of your security posture, identifying vulnerabilities that internal teams might overlook due to familiarity with the system. This includes testing for weak passwords and ensuring that strong passwords are enforced across the network.
🛡️ Comprehensive Report: Outsourced teams often provide detailed and objective reports, highlighting risks and recommendations without internal biases.
4. Proactive Approach
🔍 Continuous Improvement: Outsourcing VAPT allows for a proactive approach to security, regularly assessing the threat landscape and adjusting your digital defenses accordingly. This can help ensure that your organization is always one step ahead of potential attackers.
🔍 Comprehensive Coverage: Outsourced teams often combine automated tools with manual testing to cover all aspects of your system, including network traffic analysis and vulnerability detection, ensuring robust security management systems.
Key indicators that your product needs a VAPT assessment
Here are some key indicators that your product needs a Vulnerability Assessment and Penetration Testing (VAPT) assessment:

- New Product Launch: Before launching a new product, ensure there are no security vulnerabilities.
- Major Updates or Changes: Significant updates or changes to the product's code, architecture, or features can introduce new vulnerabilities.
- Compliance Requirements: Industry regulations and standards, like PCI-DSS and GDPR, require regular security assessments to meet regulatory compliance.
- Incident Response: Recent security breaches, successful cyberattacks, or malicious incidents may indicate underlying vulnerabilities.
- Integration with Third-Party Systems: Connecting with external systems or APIs can introduce new security risks and require robust defenses.
- Performance Issues: Unexpected performance degradation could be a sign of underlying security issues and cyber risks.
The common challenges associated with VAPTs
Here are some common challenges associated with Vulnerability Assessment and Penetration Testing (VAPT):
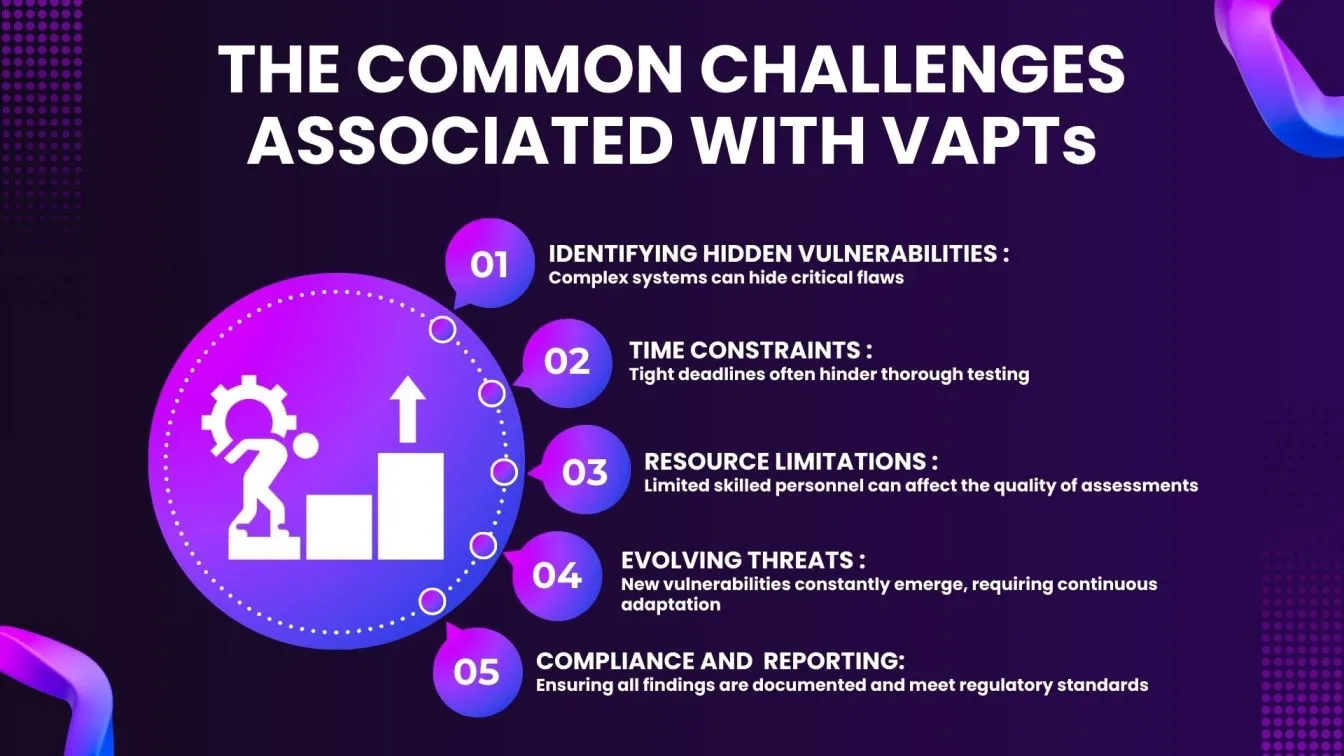
1. Resource Constraints
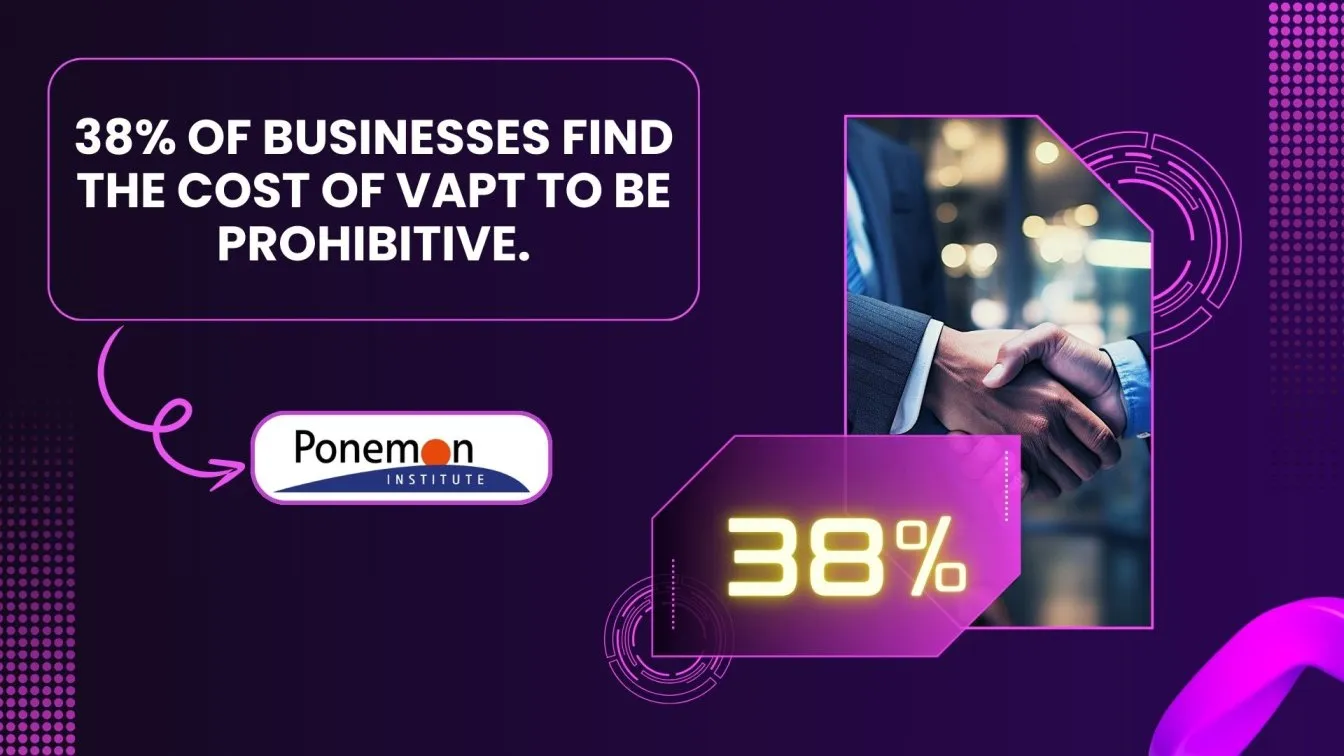
- Often, organizations have limited budgets for security testing, making it difficult to conduct comprehensive assessments and left with potential risks.
- A lack of skilled personnel can lead to incomplete or inaccurate testing.
2. Scope Definition
- Without clear goals, VAPT efforts may not address the most critical vulnerabilities.
- Identifying and excluding redundant or irrelevant areas from testing can be challenging.
3. Complex Environments
- Frequent changes in applications or infrastructure can result in moving targets for automation testing.
Best tool for vulnerability scanning

Selecting the best vulnerability scanning tool depends on your specific needs, environment, and budget. However, several tools are widely recognized for their effectiveness and capabilities. Here are some of the best tools for vulnerability scanning across various platforms:
1. Nessus
- Description: Nessus is a popular tool for scanning and identifying vulnerabilities, configuration issues, and compliance gaps.
- Key Features:
- Extensive library of plugins for finding vulnerabilities.
- Supports scanning of web apps, cloud, and network devices.
- User-friendly interface with detailed reports and fix suggestions.
2. OpenVAS
- Description: OpenVAS is an open-source vulnerability scanner that provides comprehensive scanning capabilities.
- Key Features:
- Regular updates with new vulnerability data.
- Suitable for scanning networks, servers, and web applications.
- Customizable scans and detailed reporting.
3. QualysGuard
- Description: QualysGuard is a cloud-based solution that offers continuous monitoring and vulnerability management.
- Key Features:
- Automated scanning and real-time updates.
- Covers a wide range of assets, including on-premises and cloud environments.
- Intuitive dashboard with risk prioritization.
- Description: Nexpose by Rapid7 provides powerful vulnerability scanning and potential risk assessment.
- Key Features:
- Real-time visibility and analytics.
- Integration with Metasploit for penetration testing.
- Detailed reports with actionable insights.
5. Acunetix
- Description: Acunetix is a specialized scanner for web applications and websites.
- Key Features:
- Detects vulnerabilities like SQL injection and cross-site scripting.
- Supports scanning of custom web applications.
- Provides compliance reports and vulnerability management features.
The ethical considerations involved in VAPTs

Conducting Vulnerability Assessment and Penetration Testing (VAPT) involves several ethical considerations to ensure that the process is conducted responsibly and legally. Here are some key ethical considerations:
1. Authorization and Consent
Ensure that explicit, written authorization is obtained from the organization before conducting any tests. Unauthorized testing is illegal and unethical.Clearly define and agree on the scope of the testing to avoid testing areas not approved by the organization.
2. Privacy
Handle any sensitive or personal data encountered during testing with the utmost care, ensuring it is not exposed or misused. Maintain confidentiality of any findings and sensitive information related to the organization’s security posture.
3. Minimizing Disruption
Plan tests to minimize impact on the organization’s normal operations. Avoid times of high activity or critical business operations.Assess and mitigate any potential impact of the testing on system performance or availability.
4. Legal Compliance
Ensure that all testing activities comply with relevant laws and regulations, including data protection and cybersecurity laws.Be aware of and comply with industry-specific regulations and standards that may affect the testing process.
5. Ethical Use of Findings
Report vulnerabilities and security issues honestly and accurately, without exaggerating or downplaying the risks. Provide actionable recommendations for remediation and assist in prioritizing the vulnerabilities based on risk.
Potential financial losses from security breaches

Security breaches can have severe financial impacts on organizations, affecting both their finances and long-term reputation. Here's an overview of the potential financial losses:
- Direct Financial Losses
📌 Theft of Funds: Attackers can steal money from accounts or payment systems, as seen in the 2016 Bangladesh Bank heist, where $81 million was stolen. Effective access controls are essential to prevent such losses.
📌 Ransom Payments: Organizations may be forced to pay large sums in ransomware attacks to regain access to their systems. The average ransom payment reached $1.2 million in 2023. This highlights the importance of proactive measures and robust cybersecurity defenses.
- Legal and Regulatory Costs
📌 Fines and Penalties: Non-compliance with regulations like GDPR or PCI DSS can result in hefty fines, such as the £20 million fine British Airways received for a 2018 data breach. Adhering to regulatory standards is crucial to avoid these penalties.
📌 Lawsuits and Settlements: Breaches can lead to expensive lawsuits and settlements, as seen in Equifax's $700 million settlement following their 2017 breach. Ensuring a high level of security helps mitigate these risks.
- Real-World Attack Scenario and Recovery Costs
📌 Investigation Expenses: Identifying and investigating the breach requires significant resources and expertise, including thorough traffic analysis.
📌 Remediation Costs: Fixing vulnerabilities and restoring systems often requires new software or hardware, continuous VAPT, and manual tests to prevent future issues. Implementing strong passwords and securing operating systems are essential steps in remediation.

How VAPT Helps Mitigate Risks?
Vulnerability Assessment and Penetration Testing (VAPT) is essential for modern cybersecurity strategies. By identifying and addressing vulnerabilities before they can be exploited, VAPT plays a crucial role in mitigating risks and ensuring a robust security posture. Here's how VAPT can help:

- Identifies Vulnerabilities Early: Detects weaknesses before they can be exploited, allowing for timely remediation.
- Strengthens Security Posture: Simulates attacks to assess and improve defenses against potential breaches.
- Ensures Compliance: Helps meet regulatory requirements by demonstrating proactive security measures.
- Reduces Downtime: Prevents costly disruptions by addressing in-depth analysis before they cause system outages.
- Builds Customer Trust: Enhances reputation by showing a commitment to protecting data and preventing breaches.
How can a VAPT help us improve our product's security posture?
Vulnerability Assessment and Penetration Testing (VAPT) can significantly enhance your product's security posture in the following ways:

- Finds security weaknesses and allows for quick remediation.
- Tests defenses against potential cyber threats.
- Detects misconfigurations and strengthens overall security.
- Meets industry standards and regulatory requirements.
- Offers actionable insights for a stronger security posture.
Here's a quick recap:
Throughout our discussion, we’ve emphasized the critical role of Vulnerability Assessment and Penetration Testing (VAPT) in securing your product. VAPT helps identify and address vulnerabilities, simulate real-world attacks, and ensure compliance with industry standards. Investing in VAPT is essential for enhancing your product's security in 2024. Here’s a breakdown:

- Benefits of VAPT: We’ve highlighted how VAPT identifies and fixes vulnerabilities, simulates real-world attacks, and enhances overall security configuration.
- Challenges and Considerations: We’ve addressed the common challenges associated with VAPT, including resource limitations and high costs, and provided insights into overcoming these obstacles.
- Impact on Security Strategy: We’ve examined how VAPT supports compliance with industry standards and offers actionable insights to strengthen your security posture.
By understanding these aspects, you can see why investing in VAPT is essential for robust and proactive product security in 2024.
People also asked
👉🏻 How often should VAPT be conducted on our product?
VAPT should be conducted regularly, typically every 6 to 12 months, or after major updates.
👉🏻 How does VAPT contribute to regulatory compliance for our product?
VAPT helps meet regulatory requirements by identifying and addressing security weaknesses to ensure data protection and compliance.
👉🏻 What are the goals of vulnerability management?
The goals are to identify, prioritize, and remediate security vulnerabilities to protect against potential threats.
👉🏻 What level of expertise is required to interpret and act upon VAPT findings?
High-level expertise is needed, typically from experienced security professionals or security experts, to accurately interpret and address findings.
👉🏻 How much does a VAPT typically cost?
VAPT costs vary widely but generally range from $5,000 to $50,000 depending on the scope and complexity.





%201.webp)

